What Security Measures Should We Implement to Protect Our Growing User Base?
Growing fast? Here's how to stay one step ahead of cyber threats and protect your user base.

Growth is exhilarating. Watching your user base climb is like seeing your hard work finally pay off. But growth also comes with responsibilities—big ones. Chief among them? Security.
At 1985, where we help companies build robust software solutions, we’ve seen how rapid growth can make organizations an attractive target for bad actors. If security isn’t front and center, it can unravel everything you’ve built. Let’s dive into actionable, intelligent security measures you should implement to protect your growing user base.
1. Understand Your Attack Surface
Growth means complexity. Complexity means more potential vulnerabilities. The first step in bolstering security is understanding where your risks lie.
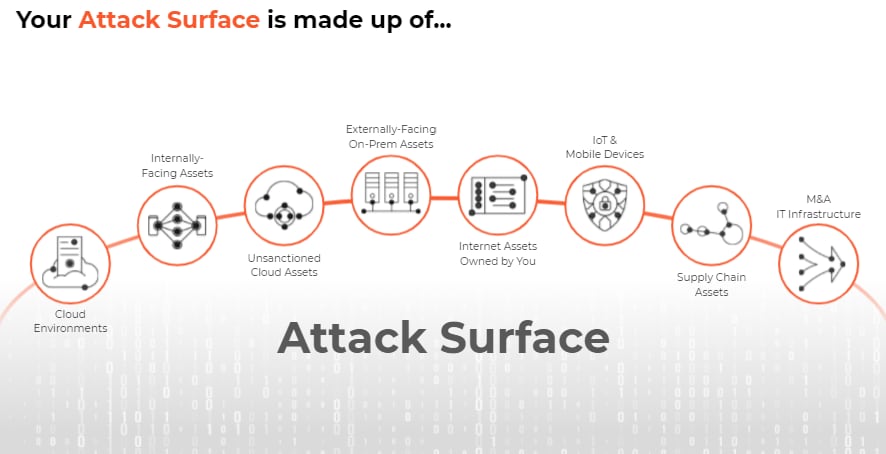
Map It Out
Imagine your application as a fortress. Every door, window, and underground tunnel is a potential entry point. APIs, third-party integrations, user data storage, and even forgotten subdomains—these all form your attack surface.
For instance, in 2021, poorly secured APIs accounted for 83% of all web application attacks, according to Gartner. That’s a staggering number and highlights why securing your APIs is critical.
Regular Security Audits
Conduct comprehensive security audits regularly. Use tools like OWASP ZAP or Burp Suite to simulate attacks on your application. These tools can reveal vulnerabilities you didn’t even know existed. A growing organization should aim for at least quarterly penetration testing to keep threats at bay.
2. Invest in User Authentication and Authorization
A solid authentication system is like a bouncer at the club. It ensures that only the right people get in.
Multi-Factor Authentication (MFA)
MFA is non-negotiable. Passwords alone are laughably inadequate—81% of hacking-related breaches stem from weak or stolen credentials (Verizon DBIR, 2022).
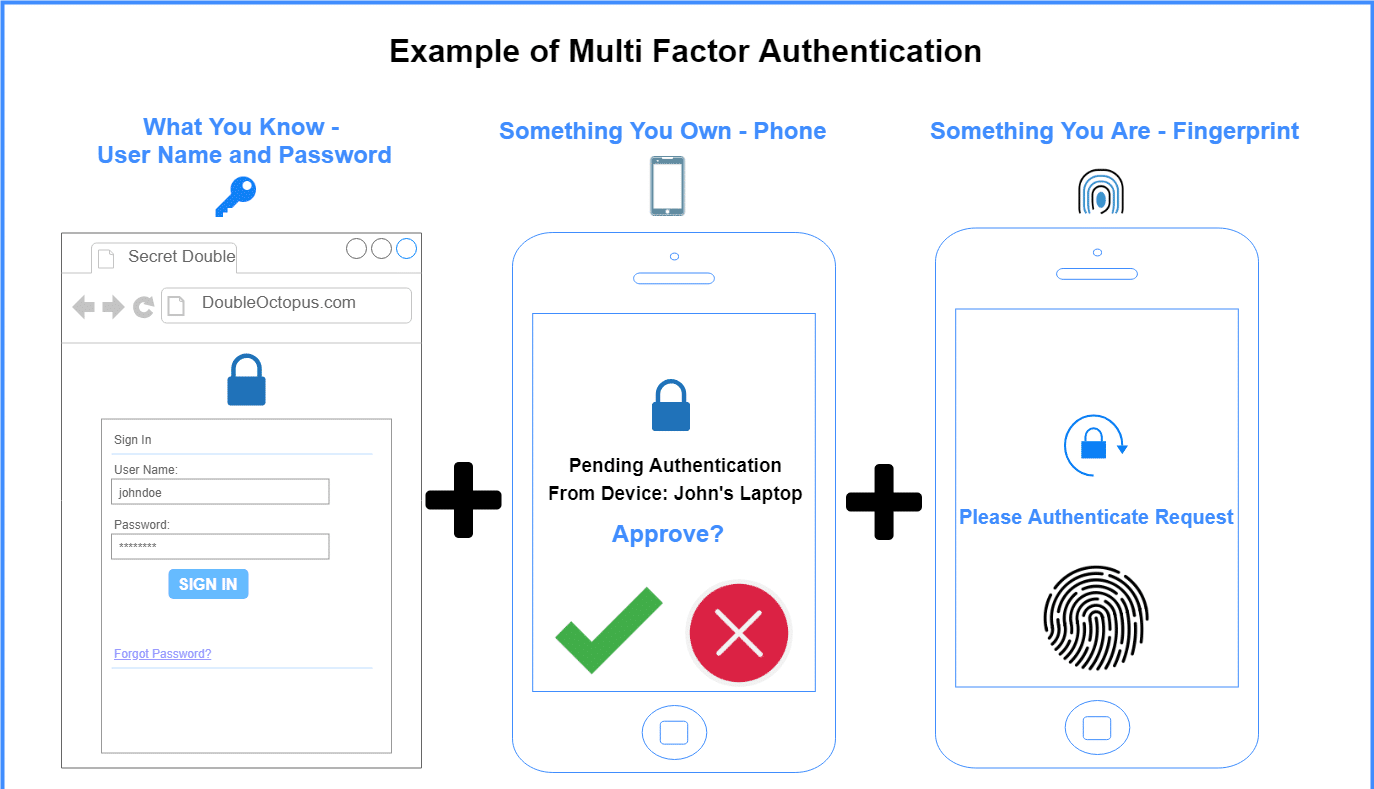
Here’s the kicker: MFA adoption rates hover around just 55% in most industries. If you’re not enforcing it, you’re lagging behind.
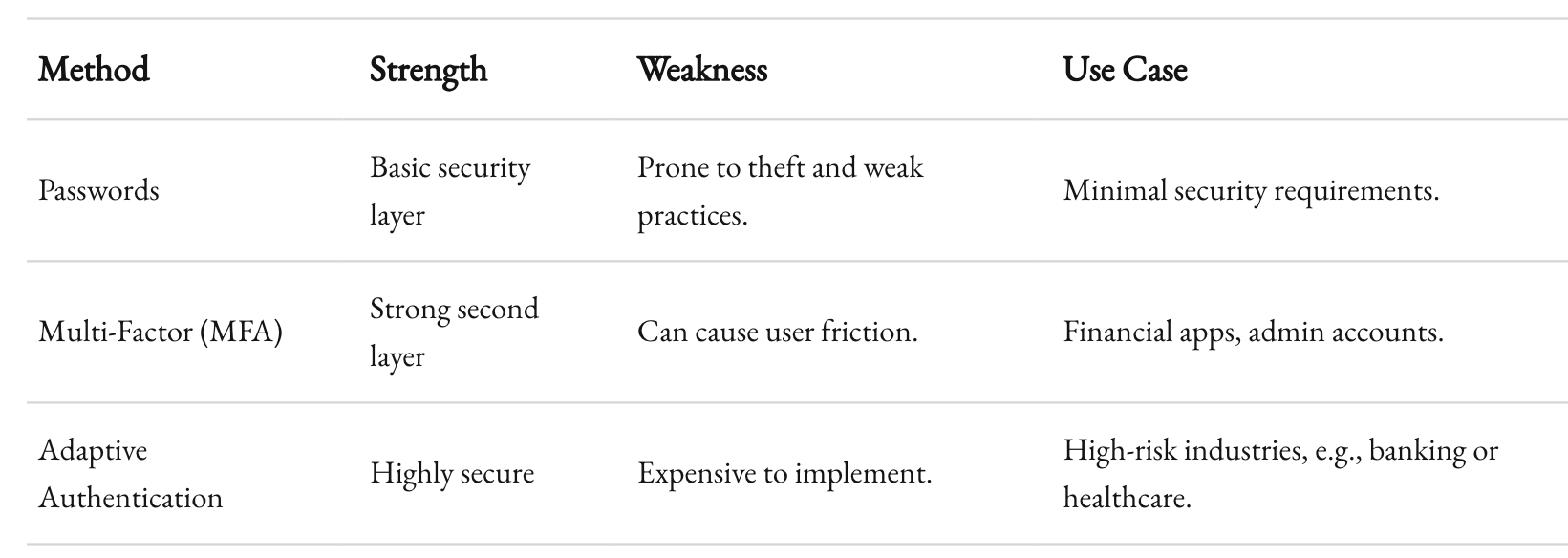
Adaptive Authentication
Take it a step further with adaptive authentication. Tools like Auth0 or Okta offer features where the system evaluates the risk of a login attempt based on factors like location, device, and user behavior. If a login looks suspicious, it triggers additional verification steps.
3. Encrypt Everything
Encryption isn’t just a checkbox. It’s your armor. Encrypting data ensures that even if bad actors get their hands on it, they can’t read it.
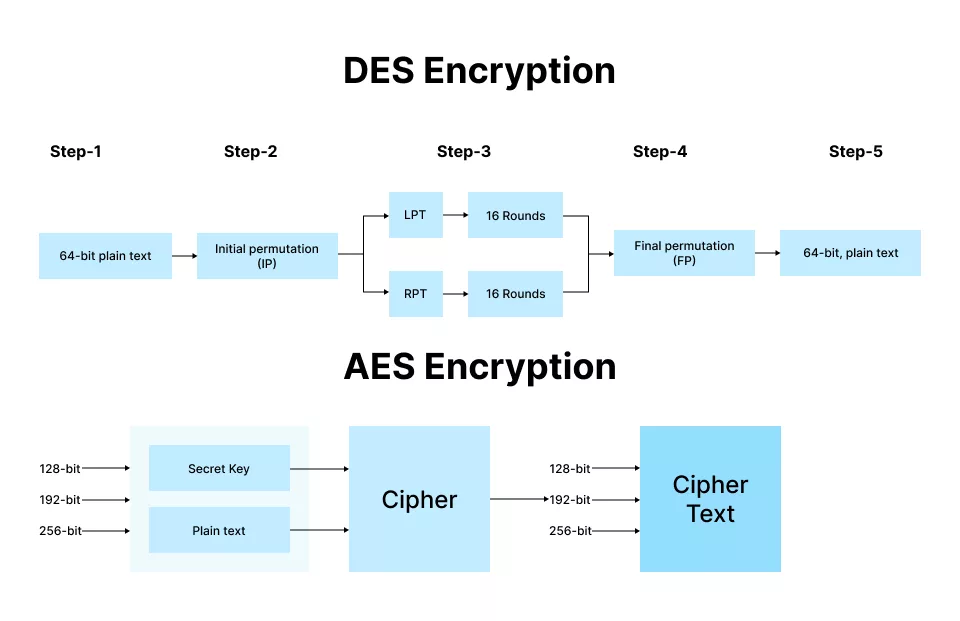
Data at Rest vs. Data in Transit
Encryption should cover both data at rest (stored data) and data in transit (data being transferred).
- For data in transit, use TLS 1.3. It’s faster and more secure than older protocols.
- For data at rest, AES-256 is the gold standard.
Zero-Trust Encryption
Consider encrypting sensitive data directly at the application layer using field-level encryption. For instance, encrypting credit card numbers or personal identifiers ensures that even if your database is compromised, sensitive fields remain secure.
4. Monitor and Respond Proactively
A reactive approach is outdated. You need to be proactive, identifying and mitigating threats before they cause damage.
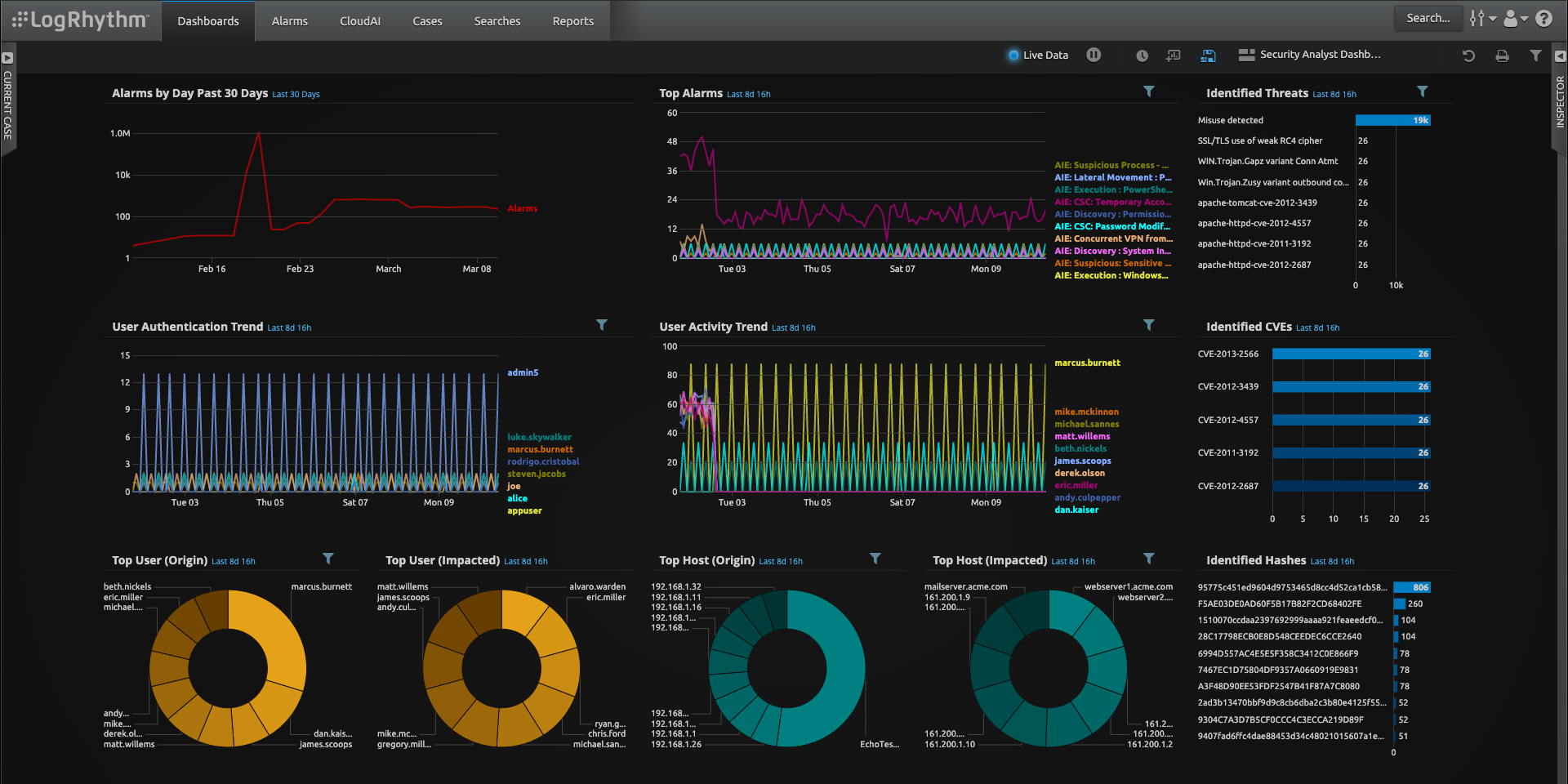
Real-Time Threat Detection
Invest in a Security Information and Event Management (SIEM) system. Tools like Splunk or Elastic Security provide real-time insights into anomalies within your infrastructure. They help identify unusual patterns, like a user suddenly downloading large datasets at 2 a.m.
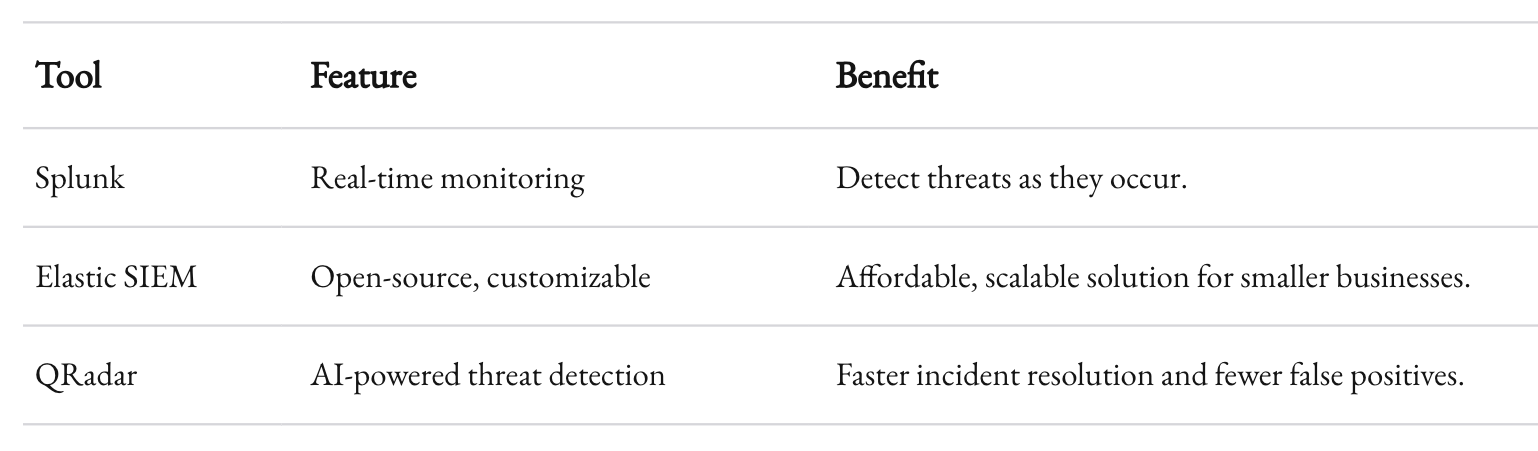
Incident Response Plan
When breaches happen—and they will—speed is everything. A robust incident response plan outlines:
- Who gets notified?
- How do you contain the breach?
- How do you communicate with affected users?
Testing this plan annually is critical. Role-play different scenarios and refine your response.
5. Secure Third-Party Integrations
Third-party tools and integrations streamline operations. But they’re also a major security risk.
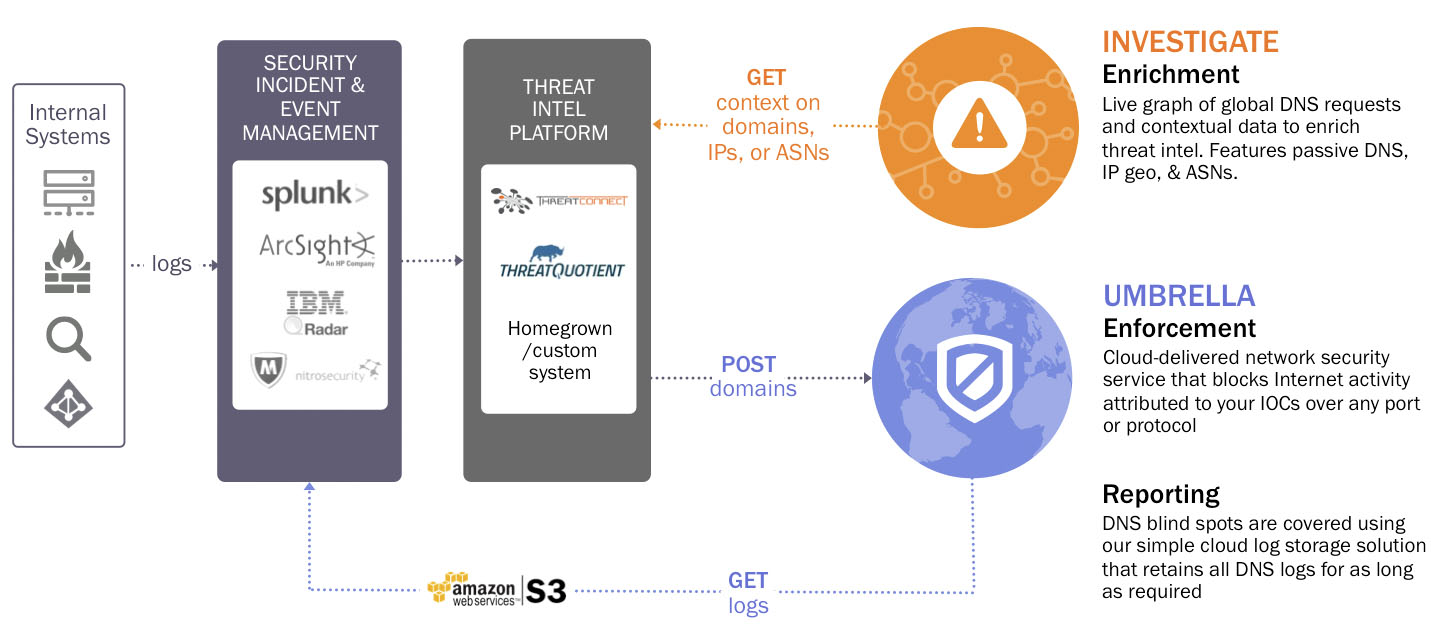
Vet Your Vendors
Run security checks on every tool you integrate. Look for certifications like SOC 2, ISO 27001, or GDPR compliance.
Principle of Least Privilege (PoLP)
When integrating third-party services, restrict their access. For example, if a payment gateway only needs transaction data, don’t give it access to user profiles or analytics dashboards.
API Gateways
Use API gateways to monitor and control API traffic. Tools like Kong or AWS API Gateway add layers of protection, such as rate limiting, authentication, and input validation.
6. Educate Your Users and Team
Humans are often the weakest link in security. Phishing, for instance, accounts for 36% of breaches (Verizon DBIR, 2022).
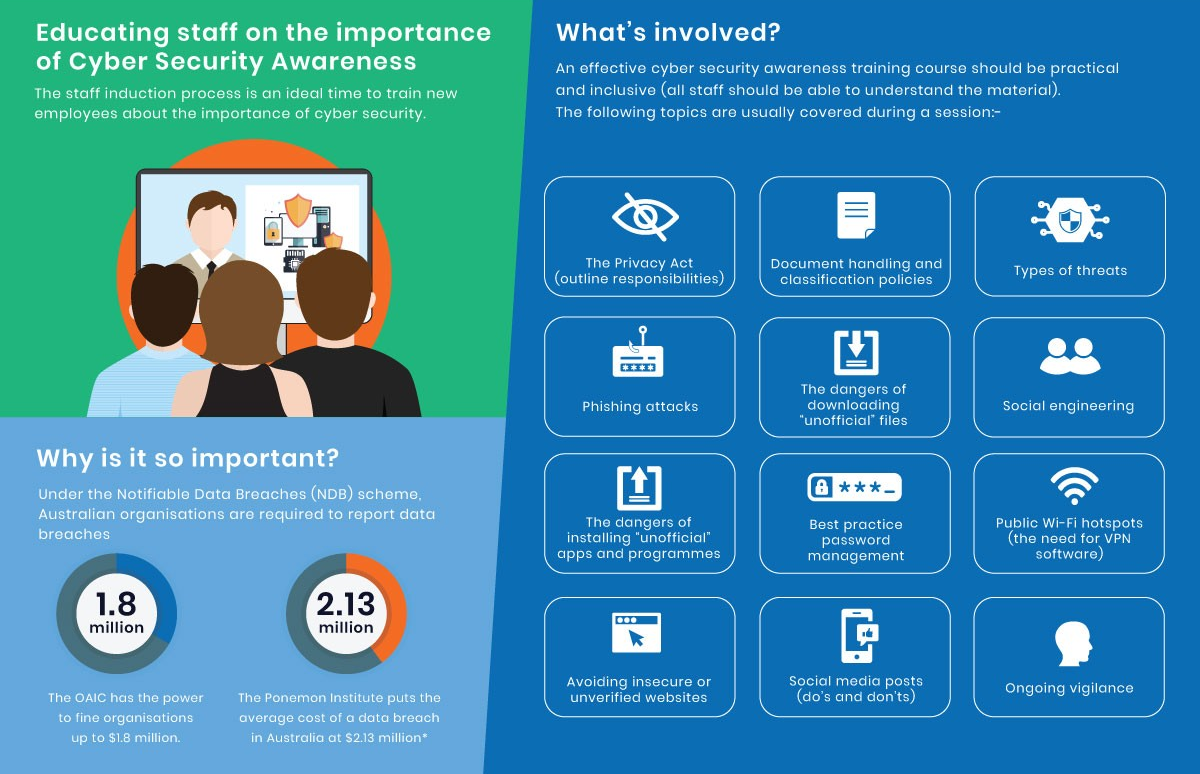
User Awareness Campaigns
Teach your users about good security hygiene. Short tutorials on recognizing phishing emails or creating strong passwords go a long way. Services like CyberSafe or KnowBe4 offer scalable solutions for user training.
Developer Best Practices
Developers need ongoing security training too. Make tools like OWASP Top Ten part of their toolkit. Regularly discuss case studies of real-world breaches to keep them aware of evolving threats.
7. Backup and Disaster Recovery
No system is bulletproof. Backups are your safety net.
Immutable Backups
Create immutable backups that can’t be altered or deleted. These ensure that even ransomware attacks can’t compromise your data.
Backup Frequency and Testing
Follow the 3-2-1 rule:
- 3 copies of your data
- 2 different media types (e.g., cloud and local storage)
- 1 copy offsite
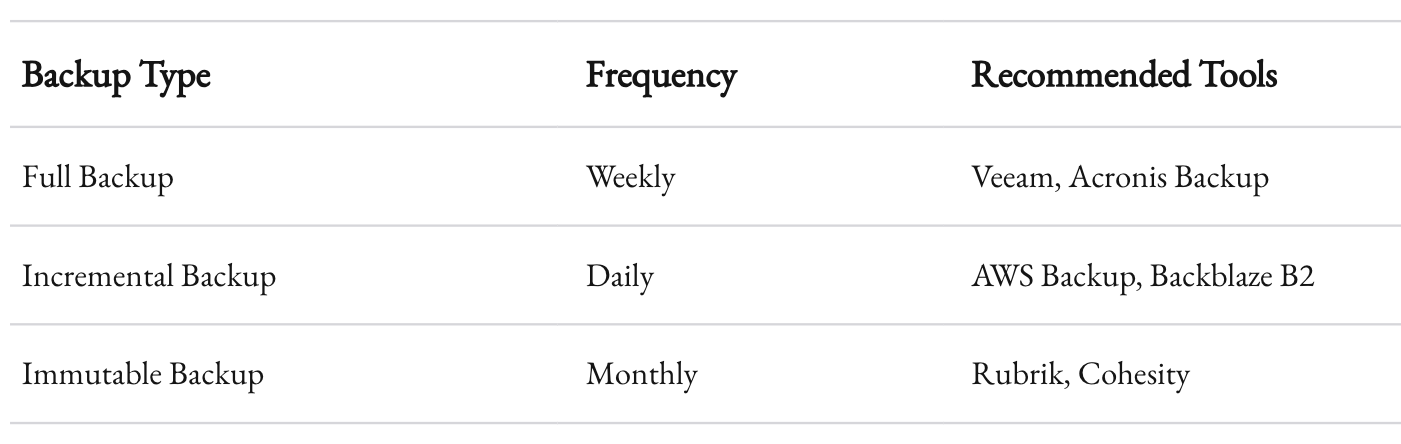
Testing backups is non-negotiable. Too many organizations discover that their backups were faulty only after a breach.
8. Adopt Zero Trust Architecture
The traditional “perimeter defense” model—where everything inside your network is trusted—is obsolete.
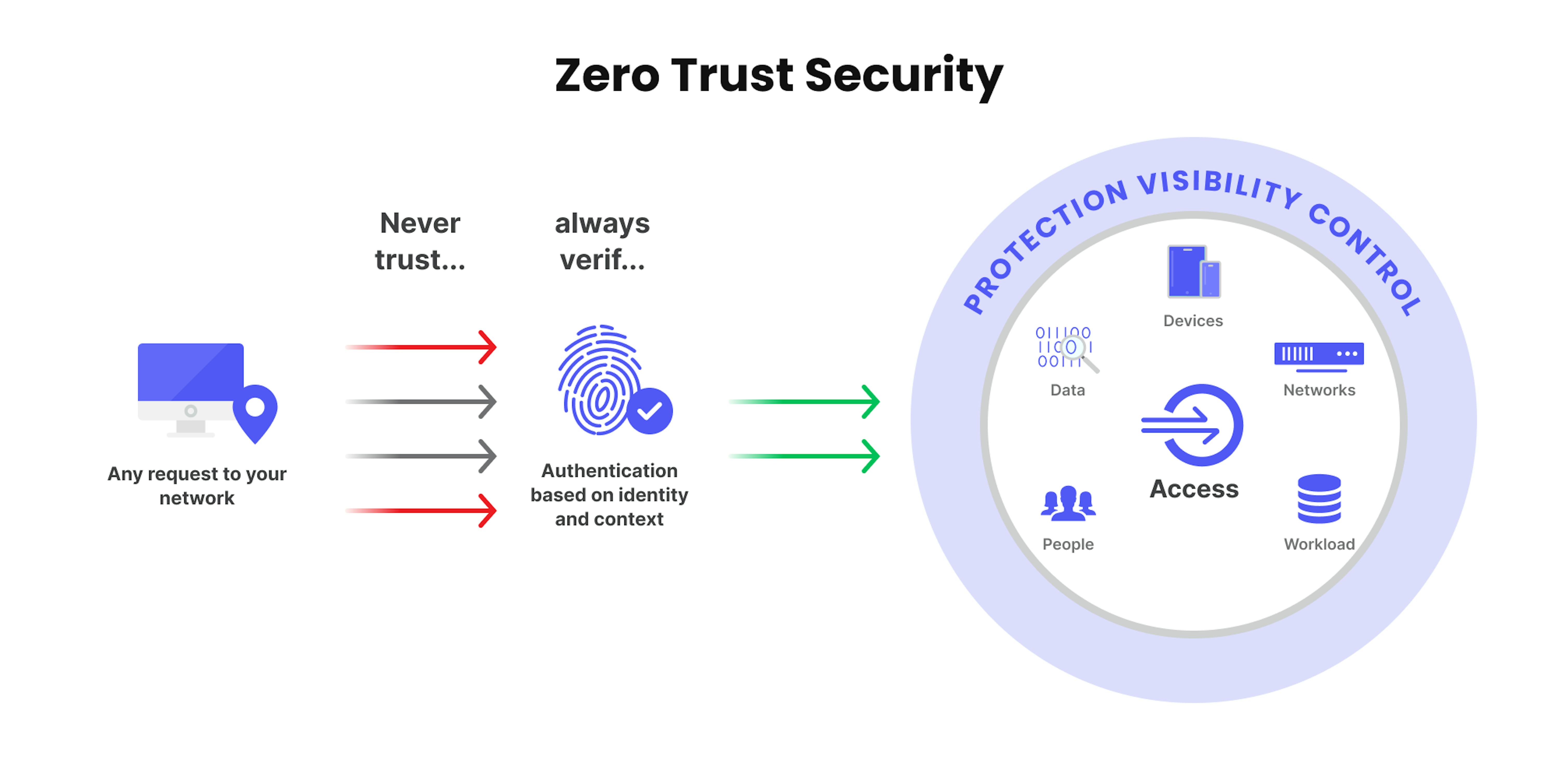
Verify, Then Trust
Zero Trust assumes that every request, even from internal users, could be malicious. Tools like Zscaler or Palo Alto Networks Prisma Access help implement Zero Trust policies.
Micro-Segmentation
Break your network into smaller zones. For example, production databases should never communicate directly with internal HR systems. This limits the damage an attacker can cause.
9. Regular Compliance Checks
Compliance isn’t just a regulatory checkbox; it’s a framework for better security.
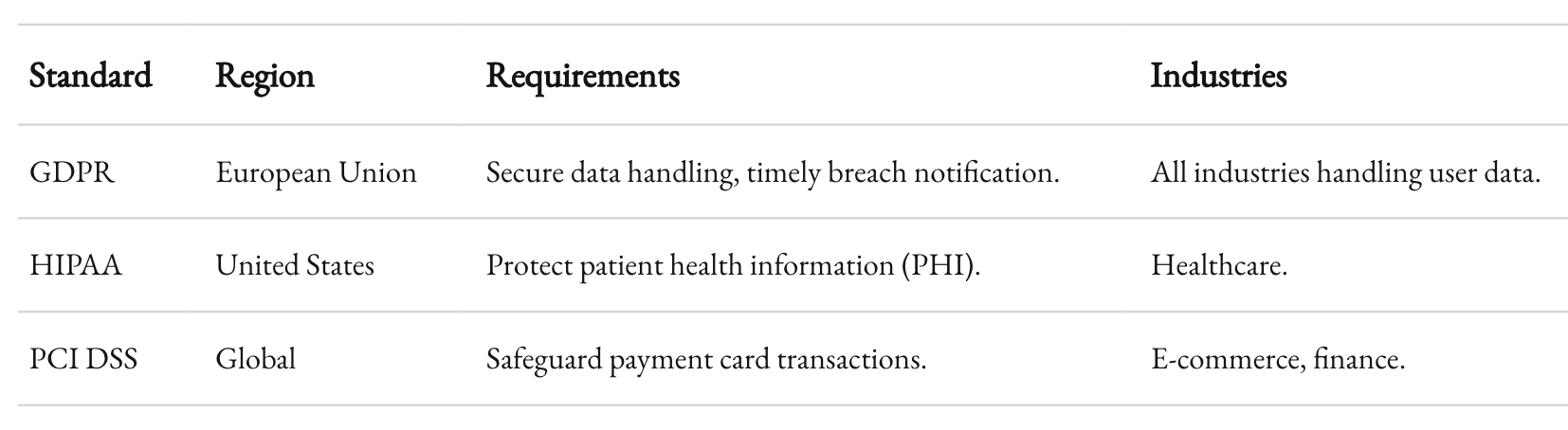
GDPR, HIPAA, and Beyond
Understand which regulations apply to your business and follow them religiously. GDPR, for example, mandates timely breach notifications and secure data handling. Non-compliance can result in fines up to 4% of annual global turnover.
Auditable Trails
Maintain detailed logs for every action. Tools like LogRhythm or Datadog can help ensure you’re audit-ready at all times.
10. Be Transparent With Your Users
Users trust you with their data. That trust is earned, not given.
Clear Communication
If a breach occurs, communicate it promptly. Explain what happened, how you’re fixing it, and what steps users should take. Transparency builds loyalty even in the face of adversity.

Privacy by Design
Bake privacy into your product from the ground up. Allow users to control how their data is used. Features like opt-in permissions or anonymized analytics show that you respect their privacy.
Recap
Protecting your user base isn’t a one-time task; it’s an ongoing commitment. At 1985, we’ve learned that the best security measures evolve with your growth. Stay vigilant, invest in the right tools, and never underestimate the power of educating your users and team. Security isn’t just a technical challenge—it’s a cornerstone of user trust. And trust is what fuels growth.



