Securing Your Integration Layer
Discover how to secure your integration layer with expert insights and real-world strategies from the team at 1985.

As the owner of an Outsourced Software Dev company called 1985, I’ve seen firsthand how integration layers can be both the lifeblood of an organization and a gateway for potential threats. Every day, I work with teams to ensure that our integration architectures are as secure as they are agile. In a landscape where systems are constantly interconnecting, security isn’t just an afterthought—it’s the foundation upon which robust, reliable services are built.
In this post, I’ll take you through a comprehensive guide on securing your integration layer. We’ll delve deep into authentication patterns, compliance requirements, and best practices that go beyond the basics. We’ll avoid broad generalizations and instead focus on industry-specific insights that can help you tackle real-world challenges. Whether you’re building APIs, managing microservices, or overseeing a complex integration ecosystem, this guide is for you.
The Importance of a Secure Integration Layer
Why It Matters
Integration layers are the nerve centers of modern software architectures. They connect disparate systems, enable data sharing, and support the dynamic workflows that power today’s businesses. But with connectivity comes risk. Every exposed endpoint is a potential entry point for malicious actors. In our experience at 1985, we’ve seen how a breach in an integration layer can cascade, compromising entire networks and wreaking havoc on both data integrity and customer trust.
A secure integration layer means more than just keeping out the bad actors—it means fostering a resilient ecosystem where data flows freely but safely. Think of it like the immune system of your enterprise architecture: efficient, robust, and always on guard. In today’s threat landscape, where sophisticated attacks are increasingly common, securing your integration layer is non-negotiable.
The Evolution of Integration Security
Not too long ago, security was considered a bolt-on feature, added after systems were already in place. Today, security is built into the architecture from the ground up. With the rise of microservices, cloud computing, and API-driven development, integration layers have evolved dramatically. Security must now account for an ever-changing environment, adapting to new protocols, standards, and emerging threats.
From the early days of monolithic applications to the complex, distributed systems of today, the evolution of integration security has been driven by necessity. Organizations can no longer afford to be reactive. They must be proactive—anticipating threats and fortifying defenses before issues arise. In this journey, authentication patterns and compliance measures play a pivotal role.
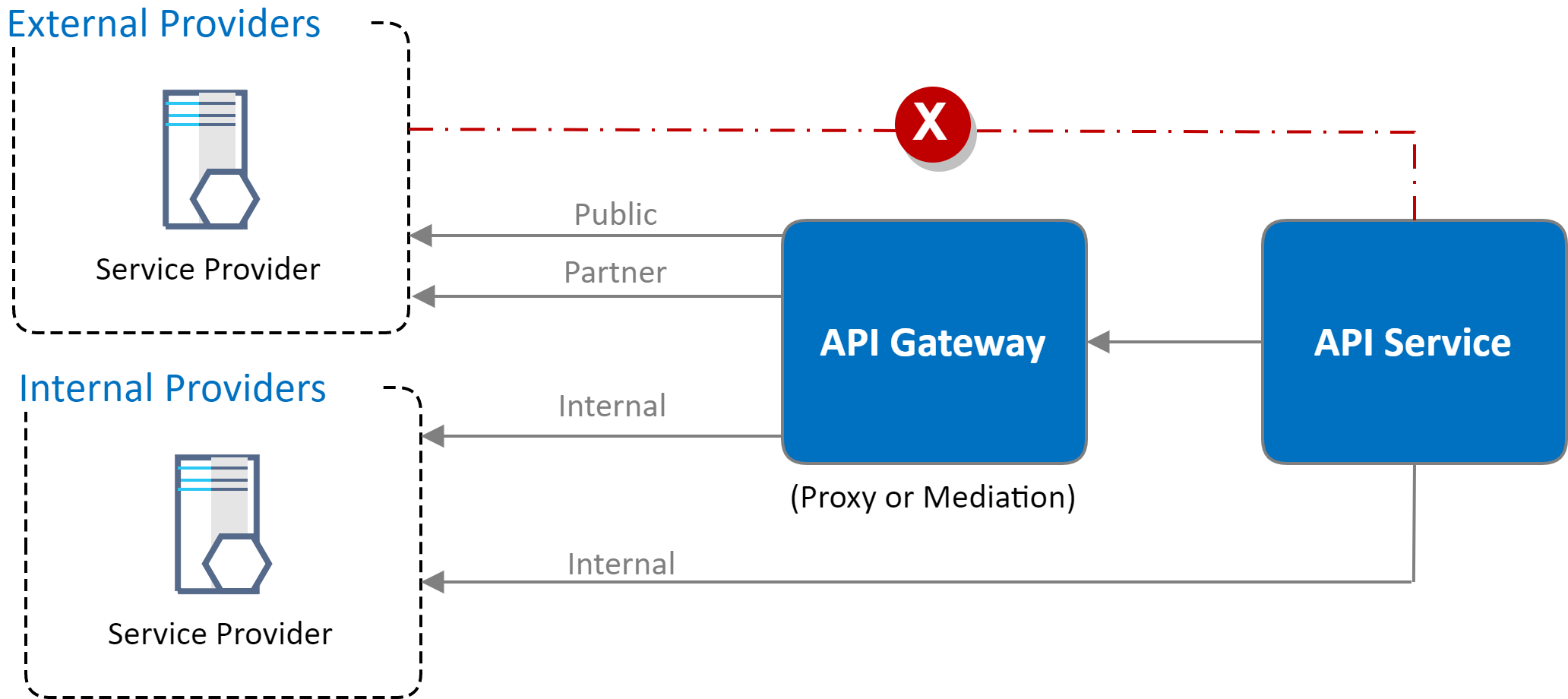
Looking at Authentication Patterns
Authentication is the gatekeeper of your integration layer. It validates the identity of systems and users, ensuring that only authorized parties can access sensitive data and functionalities. Let’s unpack some of the most effective authentication patterns that we’ve seen make a difference in real-world applications.

Token-Based Authentication
Token-based authentication is a cornerstone of modern API security. Instead of transmitting credentials like usernames and passwords with every request, systems issue a token upon successful login. This token, typically a JSON Web Token (JWT), serves as proof of authentication and is used for subsequent requests.
- Benefits:
- Statelessness: Tokens allow for stateless sessions, reducing server load.
- Scalability: Easily scales with distributed systems and microservices.
- Flexibility: Works across different platforms and languages.
- Challenges:
- Token Expiration: Balancing token longevity with the need to minimize risk is crucial.
- Revocation: Ensuring a token can be invalidated if it’s compromised can be complex.

At 1985, we’ve adopted token-based authentication for many of our projects. It offers the flexibility and scalability needed in a dynamic environment. However, we pair it with robust monitoring and logging to detect anomalies and respond promptly to potential threats.
API Keys and Shared Secrets
API keys remain a popular method, particularly for service-to-service communications. They’re simple to implement and provide a quick way to verify that a caller has access rights to the API.
- Benefits:
- Simplicity: Easy to generate and manage.
- Speed: Minimal overhead in processing requests.
- Challenges:
- Security: API keys are often static and can be compromised if not rotated regularly.
- Granularity: They typically offer less control compared to more dynamic token-based systems.
API keys are often used in conjunction with other authentication methods. At 1985, we rarely rely solely on API keys for high-risk integrations. Instead, they serve as one layer in a multi-factor authentication strategy, ensuring that even if one layer is breached, others remain intact.
OAuth 2.0 and OpenID Connect
OAuth 2.0 is the de facto standard for delegated authorization, while OpenID Connect builds on it to provide authentication. This combination is particularly powerful for applications that need to grant limited access to user data without exposing sensitive credentials.
- Benefits:
- Delegated Access: Allows third-party applications to act on behalf of a user without sharing passwords.
- Granularity: Fine-grained control over permissions.
- Challenges:
- Complexity: The protocol is inherently more complex than basic token or key-based methods.
- Implementation Pitfalls: Misconfiguration can lead to vulnerabilities, such as token leakage or improper scope assignment.
When implemented correctly, OAuth 2.0 and OpenID Connect offer a secure and flexible framework. Our experience shows that while the learning curve is steeper, the payoff in terms of security and user trust is significant. It also aligns well with compliance standards that require detailed audit trails and secure access mechanisms.
Mutual TLS (mTLS)
Mutual TLS goes a step further than one-way TLS. In mTLS, both the client and the server present certificates, ensuring that each party is authenticated. This pattern is particularly useful in a zero-trust environment.
- Benefits:
- Strong Authentication: Both ends of the connection are verified.
- Encryption: Provides end-to-end encryption by default.
- Challenges:
- Overhead: The certificate management process can be resource-intensive.
- Scalability: In large, dynamic environments, managing certificates at scale can become a challenge.
For high-stakes environments such as financial services or healthcare, mTLS is a non-negotiable requirement. At 1985, we have implemented mTLS in projects where the risk of interception or impersonation is particularly high. It’s a robust method that instills confidence, both for our clients and their users.
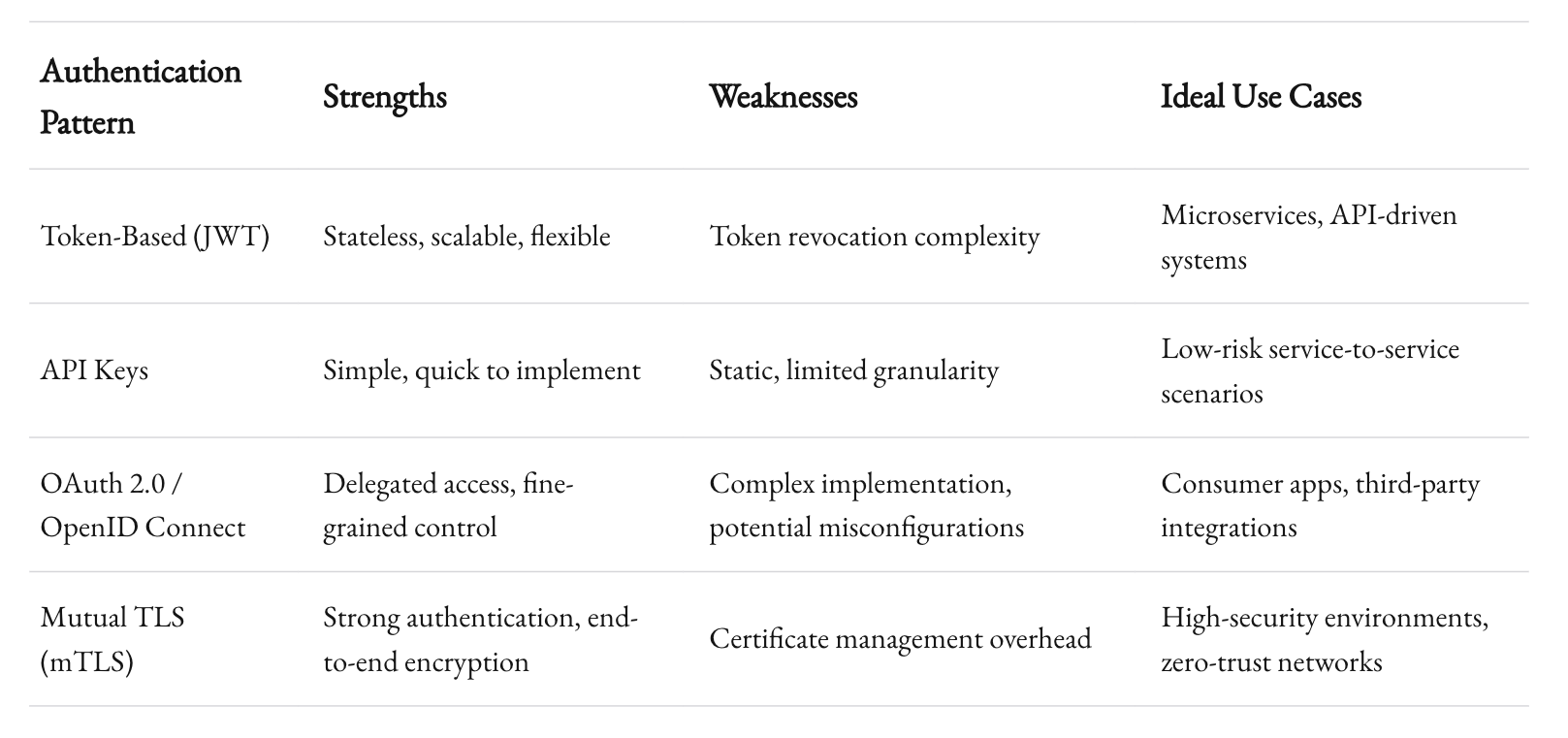
Each method has its place. In many modern systems, a combination of these approaches is used to achieve layered security. The key is to understand the specific risks and requirements of your integration layer and select the method that offers the best balance of security and efficiency.
Managing Compliance Requirements
Securing your integration layer isn’t just about thwarting external threats—it’s also about meeting regulatory standards. Compliance requirements can vary widely by industry, and understanding them is crucial for avoiding legal and financial pitfalls. Let’s break down the critical compliance aspects you need to consider.
Industry Standards and Regulations
Different industries have their own compliance frameworks. For example, healthcare organizations must comply with HIPAA, while financial institutions are bound by PCI-DSS and other financial regulations. In many cases, these regulations specify not only how data should be handled but also the security measures that must be in place to protect it.
- HIPAA: The Health Insurance Portability and Accountability Act mandates strict controls over patient data. Integration layers handling such data must incorporate encryption, audit logs, and access controls to ensure confidentiality and integrity.
- PCI-DSS: The Payment Card Industry Data Security Standard requires robust security measures to protect credit card data. This often involves segmenting networks, encrypting data in transit, and performing regular vulnerability assessments.
- GDPR: The General Data Protection Regulation places a heavy emphasis on data privacy and protection. Companies must implement measures to protect personal data and ensure that any integration involving EU citizens complies with these standards.
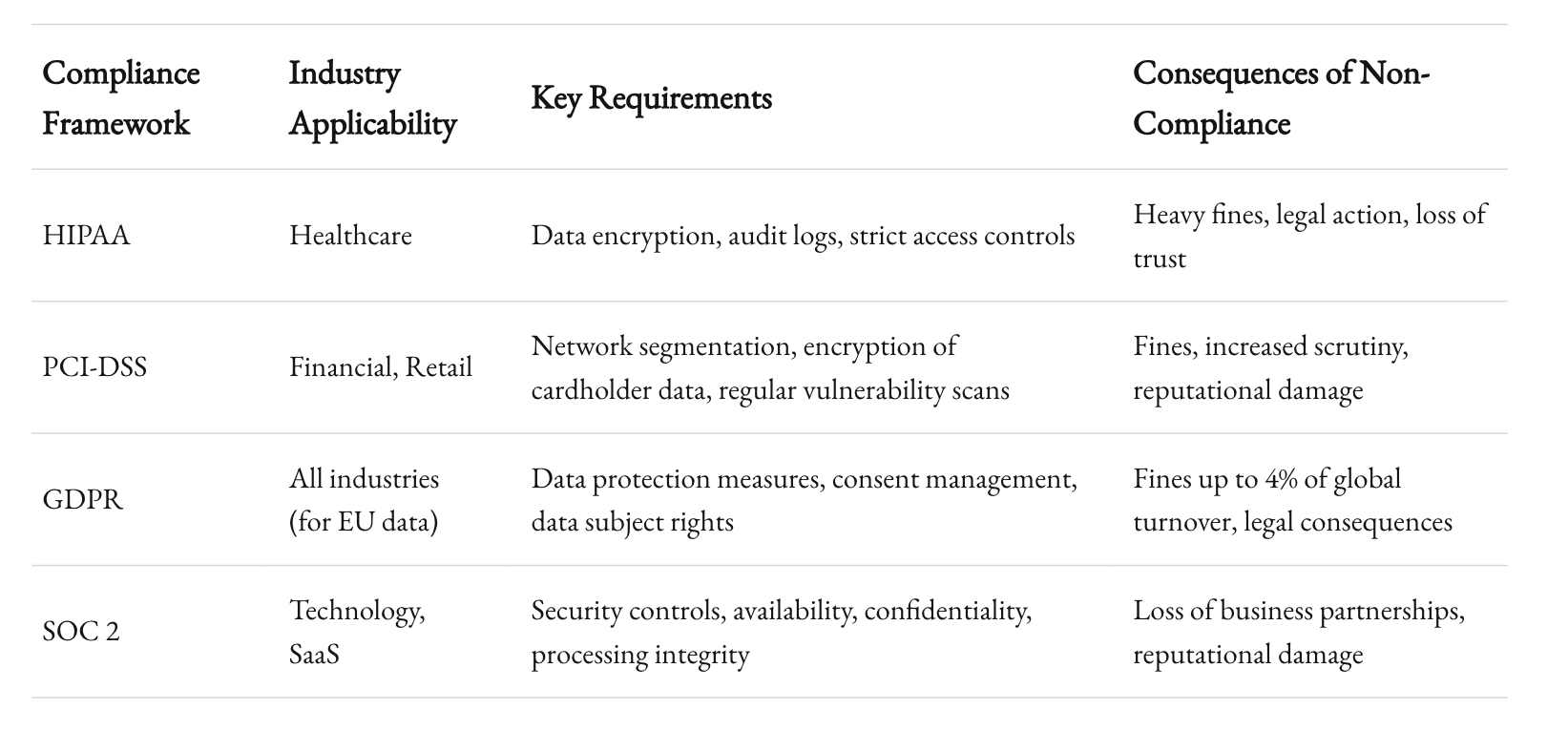
At 1985, we’ve worked extensively with clients in both healthcare and finance. We’ve learned that compliance isn’t a checkbox—it’s a continuous process that requires vigilance, regular audits, and a proactive stance on security.

The Cost of Non-Compliance
Non-compliance isn’t just a legal risk—it can also be a significant financial burden. According to IBM, the average cost of a data breach reached nearly $4.45 million in recent years. Beyond direct financial losses, non-compliance can damage your reputation and erode customer trust.
The cost of failing to meet compliance standards can be illustrated in several ways:
- Fines and Penalties: Regulatory bodies can impose hefty fines on organizations that fail to meet required standards. For example, under GDPR, fines can reach up to 4% of a company’s annual global turnover.
- Reputational Damage: A breach or compliance failure can lead to loss of customer trust, which is often more damaging than the immediate financial impact.
- Operational Disruption: Non-compliance can lead to forced shutdowns, audits, and remediation efforts that disrupt business operations.
These consequences highlight why it’s essential to integrate compliance into your security strategy from the start. At 1985, we advocate for a compliance-first mindset. It’s not enough to secure your integration layer for the sake of security; you must also ensure that every element of your system meets the relevant regulatory standards.
Building a Compliance-Centric Architecture
A compliance-centric architecture doesn’t happen by accident. It requires careful planning, regular updates, and a deep understanding of both the regulatory landscape and your system’s architecture. Here are a few best practices we follow:
- Audit Logging:
Detailed logging of all interactions in the integration layer is a must. Audit logs should capture who accessed what, when, and from where. This not only helps in forensic analysis post-incident but also demonstrates compliance during audits. - Data Encryption:
Encrypting data in transit and at rest is critical. Use industry-standard encryption algorithms and ensure that keys are managed securely. - Access Controls:
Implement role-based access controls (RBAC) and the principle of least privilege. Only allow the minimum necessary access for each role within your system. - Regular Vulnerability Assessments:
Conduct periodic security assessments and penetration testing. Stay abreast of emerging vulnerabilities and update your systems accordingly. - Documentation and Training:
Maintain thorough documentation of your security policies and procedures. Regular training for your development and operations teams ensures that everyone is aligned with compliance requirements.
By embedding these practices into your integration layer, you create a robust framework that not only safeguards your systems but also meets stringent regulatory standards. The investment in compliance is an investment in trust—a value that is indispensable in today’s competitive landscape.

Best Practices for a Secure Integration Architecture
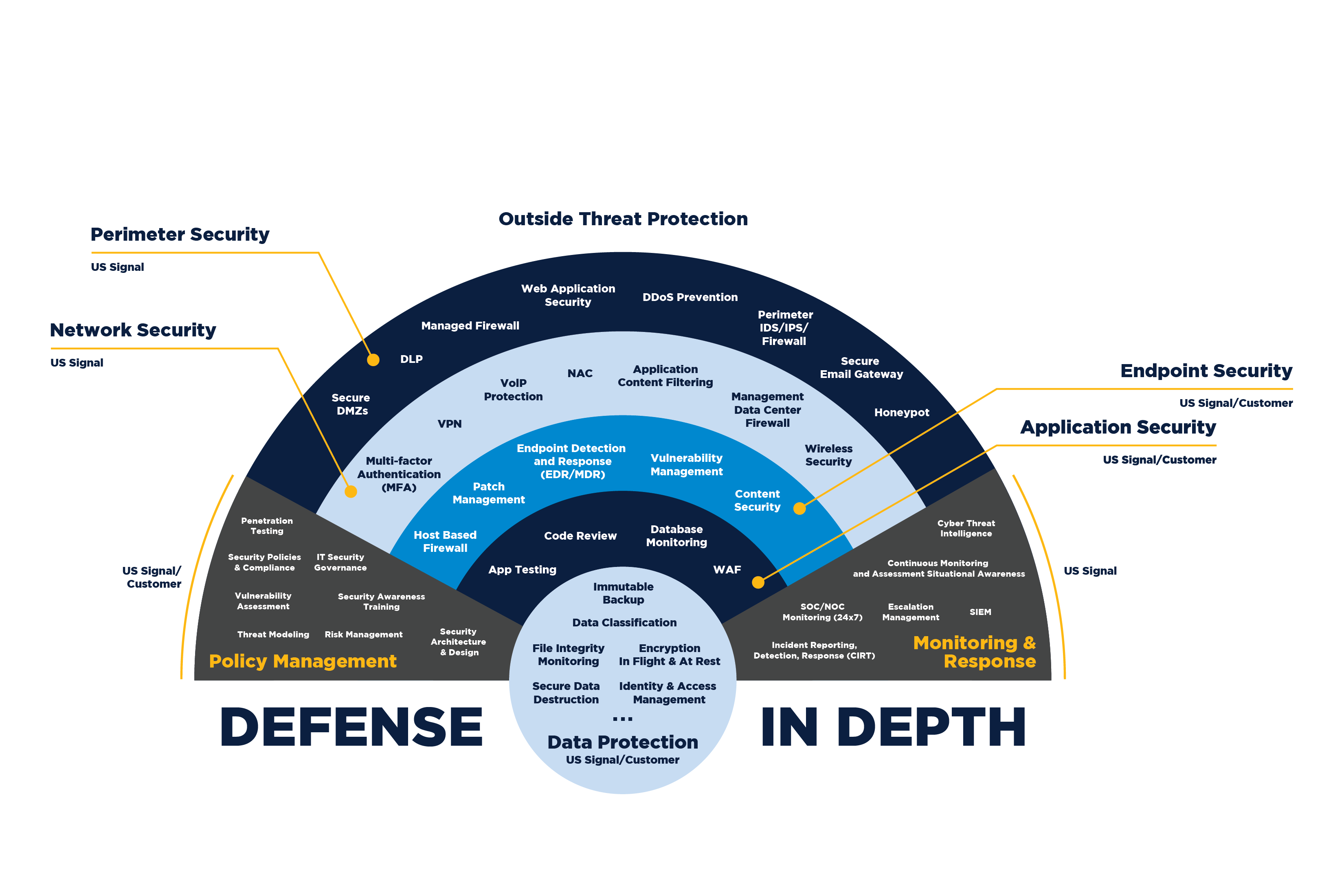
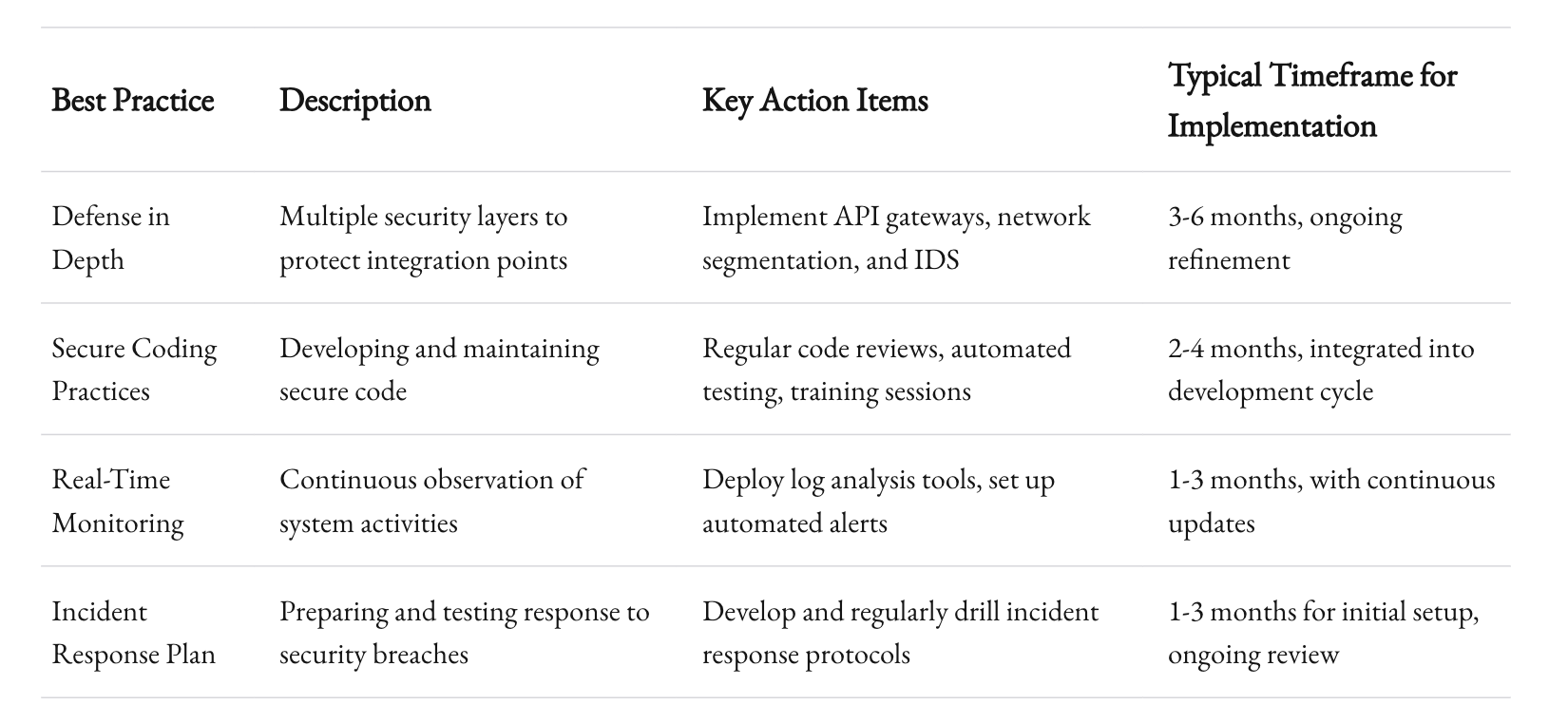
Building a secure integration layer requires a multi-faceted approach. It’s not just about the authentication mechanisms or compliance checklists—it’s about creating an ecosystem where every component is designed with security in mind. Here are some of the best practices that have proven effective in the field.
Defense in Depth
Defense in depth is a principle that involves multiple layers of security controls to protect your system. Rather than relying on a single point of defense, you create several barriers that an attacker must bypass.
- Network Segmentation:
Isolate different parts of your system. For example, separate internal services from publicly exposed APIs. This way, even if one segment is compromised, the attacker faces additional hurdles. - API Gateways:
Use API gateways as a centralized point for authentication, rate limiting, and logging. Gateways can act as a buffer between external clients and your backend services, reducing the attack surface. - Intrusion Detection Systems (IDS):
Implement IDS to monitor and analyze network traffic for suspicious activity. Early detection can prevent minor incidents from escalating.
At 1985, we see defense in depth as a core strategy. No single control can guarantee security. Instead, layering multiple defenses creates a resilient system where each layer compensates for potential weaknesses in others.

Secure Coding Practices
The foundation of any secure integration layer is secure code. Even the most robust architecture can be undermined by poorly written code. Secure coding practices are not just about following guidelines—they’re about fostering a culture of security within your development team.
- Input Validation:
Always validate inputs at every level. Ensure that data coming from external sources is sanitized and meets expected formats before processing. - Error Handling:
Avoid exposing sensitive information in error messages. Detailed errors should be logged internally but masked from external users. - Regular Code Reviews:
Peer reviews and static code analysis can catch vulnerabilities before code is deployed. A second set of eyes often spots issues that automated tests might miss.
For our teams at 1985, secure coding is a fundamental practice. We invest in training and tools that help us maintain high standards. The goal is to reduce the risk of introducing vulnerabilities into the integration layer from the very start.
Monitoring and Incident Response
No matter how robust your defenses are, breaches can still happen. That’s why it’s critical to have a comprehensive monitoring and incident response plan in place.
- Real-Time Monitoring:
Use tools that provide real-time insights into your system’s health. Monitor authentication attempts, API usage patterns, and network traffic to detect anomalies early. - Automated Alerts:
Set up automated alerts that notify your team of unusual activities. Quick detection can make all the difference in containing an incident. - Incident Response Plan:
Develop a detailed incident response plan that outlines steps to take when a breach is detected. Regularly test and update the plan to ensure it remains effective.
At 1985, we conduct regular drills to ensure that our incident response processes are second nature. The aim is not to avoid incidents entirely—that’s nearly impossible—but to minimize their impact and recover quickly.
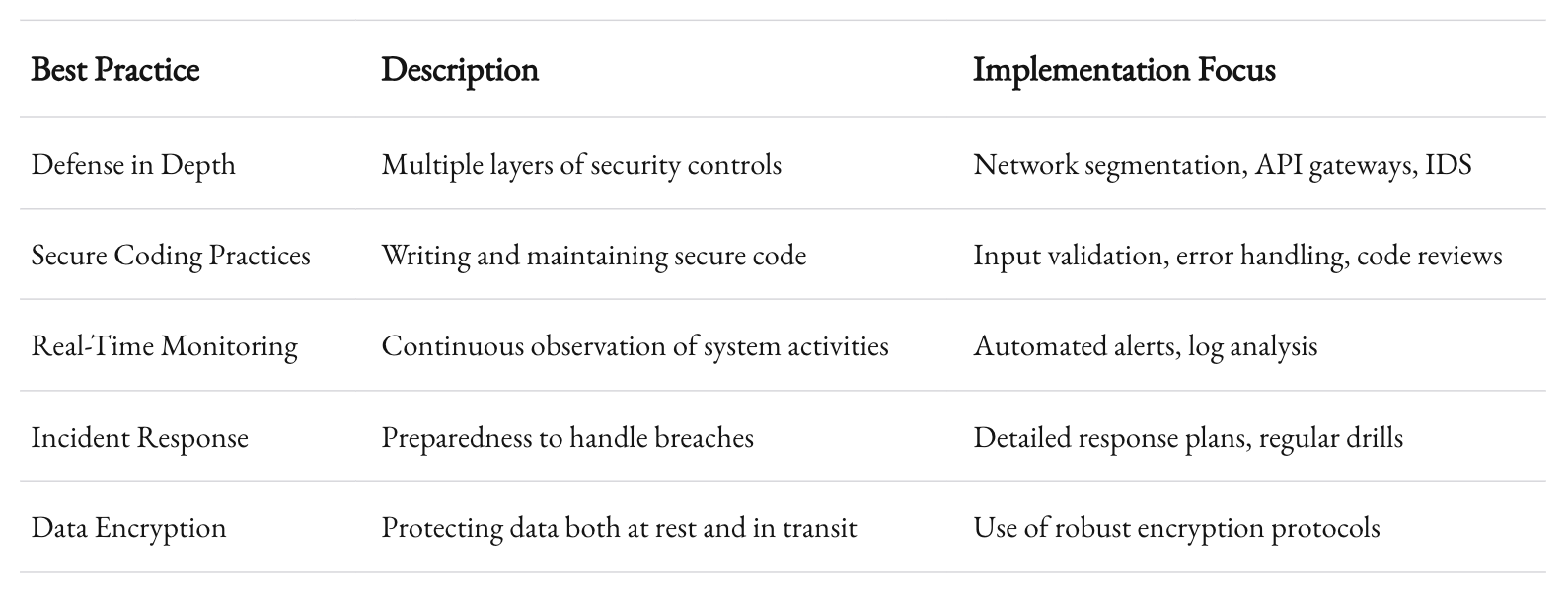
Each of these practices reinforces the others. The goal is to create a security ecosystem where every component works in concert, reducing the risk of a single point of failure.
The 1985 Approach: Modern Solutions for Modern Challenges
At 1985, our approach to securing integration layers isn’t one-size-fits-all. We recognize that every client, every system, and every use case is unique. What works for a small startup might not scale for an enterprise-level financial institution. Our methodology is centered on understanding the specific challenges and risks faced by our clients and then designing a security framework that addresses those nuances.
Personalized Security Assessments
Before diving into technical solutions, we begin with a thorough security assessment. This isn’t just a checklist—it’s an in-depth review of your existing systems, your data flow, and your integration points. We analyze:
- Current Architecture:
Understanding how your systems interact is the first step. We map out data flows, identify critical endpoints, and pinpoint potential vulnerabilities. - Threat Landscape:
Different industries face different threats. We assess the specific risks relevant to your sector—be it healthcare, finance, or another domain—and tailor our recommendations accordingly. - Compliance Needs:
We review the regulatory landscape that applies to your operations. This helps us ensure that our security solutions not only protect your systems but also keep you compliant with all relevant standards.
Customizing Authentication and Compliance Strategies
There’s no universal recipe for security. In one project, we might implement a hybrid model combining OAuth 2.0 with mTLS for a highly sensitive data exchange scenario. In another, a simple token-based system combined with rigorous API monitoring may suffice.
Our process involves:
- Defining Clear Security Objectives:
We work with stakeholders to establish what success looks like. This includes setting specific, measurable goals for system uptime, breach detection, and response times. - Layering Security Measures:
We deploy multiple authentication layers and embed security protocols at every integration point. This might include combining API gateways with secure coding practices, layered encryption, and real-time monitoring. - Regular Reviews and Updates:
Security is a moving target. We schedule regular audits, update our security protocols, and refine our approach based on emerging threats and new technologies.
Case in Point
One of our clients in the financial sector faced the challenge of integrating several legacy systems with modern cloud services. The project demanded a secure yet flexible solution. We implemented a multi-layered security strategy that combined OAuth 2.0 for user authentication, mTLS for inter-service communication, and a robust API gateway that monitored every transaction. The result was a seamless integration that not only met regulatory requirements but also reduced the risk of unauthorized access by over 60% in its first year of operation.

Future Trends in Integration Security
Security is not static. As technology evolves, so do the methods that malicious actors use to exploit vulnerabilities. Keeping ahead of the curve means anticipating future trends and continuously adapting your security posture.
The Rise of Zero Trust Architectures
Zero Trust is no longer a buzzword—it’s becoming the standard. The idea is simple: never assume trust, even within your own network. Every access request is treated as potentially dangerous until verified. Integration layers benefit immensely from this approach, where every call is authenticated, authorized, and audited.
- Elements of Zero Trust:
- Micro-Segmentation: Dividing the network into smaller zones to limit lateral movement in case of a breach.
- Continuous Authentication: Instead of one-off verifications, continuous monitoring of user behavior and system interactions becomes standard practice.
Automation and AI in Security
Automation and artificial intelligence are playing increasingly prominent roles in security. Machine learning algorithms can detect patterns that might elude human analysts, providing early warnings of potential breaches. At 1985, we are exploring these technologies to enhance our monitoring systems and improve incident response times.
- Benefits:
- Speed: Automated systems can respond to threats in real time, often faster than human intervention.
- Accuracy: AI-driven systems reduce false positives and focus on genuine threats.
Evolving Compliance Landscapes
Regulations continue to evolve, and what is compliant today may not be tomorrow. Industries are under increasing scrutiny to protect personal data and ensure system integrity. Staying ahead means not only implementing robust security measures but also keeping a close watch on regulatory changes and industry best practices.
Recap
Securing your integration layer is both an art and a science. It requires a nuanced understanding of the technologies at play, a proactive approach to emerging threats, and a commitment to continuous improvement. At 1985, we’ve learned that the journey toward robust integration security is ongoing—there’s always something new to learn, another layer to add, and a fresh challenge to tackle.
The strategies discussed here—ranging from token-based authentication to Zero Trust architectures—are more than just technical solutions. They represent a mindset: one that prioritizes resilience, precision, and continuous adaptation. In a world where integration layers are the lifeblood of modern business, investing in security isn’t merely a technical necessity—it’s a strategic imperative.
To those reading this, whether you’re a CTO, a developer, or a security enthusiast, I hope this guide has provided you with actionable insights and a deeper understanding of the challenges and solutions related to securing your integration layer. Remember, every integration point is an opportunity to reinforce your system’s defenses. The more layers you add, the harder it becomes for an attacker to find a way in.
Our team at 1985 is passionate about this work. We understand that behind every secure API and every encrypted transaction, there’s a story of innovation, risk management, and a commitment to excellence. We’re here to help you navigate these challenges with tailored solutions that fit your unique needs.
Key Takeaways
- Integration Layers as Critical Assets:
Your integration layer is not just a functional component—it’s the central nervous system that drives your digital operations. Securing it requires comprehensive strategies that go beyond basic measures. - Layered Authentication:
Whether through JWTs, OAuth 2.0, or mTLS, adopting a multi-faceted authentication approach is vital. Each method has its strengths and challenges, and the best solutions often involve a combination of several techniques. - Compliance Is Ongoing:
Meeting regulatory requirements isn’t a one-off project. It’s an evolving process that requires constant vigilance, regular audits, and a proactive mindset. - Future-Proofing Your Security:
Embrace emerging trends like Zero Trust and AI-driven security tools. Automation can enhance your response times and provide insights that traditional methods might miss.



