Safeguarding Your Intellectual Property When Working with External Developers
Worried about your IP walking out the door? Learn how to collaborate fearlessly with external developers.

I've seen things. Brilliant ideas stolen. Startups crumbling overnight. All because someone got careless with their code.
It was a Tuesday afternoon when I got the call. Another founder, voice trembling, realizing their "trusted partner" had walked away with their core algorithm. I've been there. We've all been there. In this wild west of tech, where innovation is currency and ideas spread faster than wildfire, how do you keep your digital crown jewels safe?

Let me tell you, it's not easy. But it's not impossible either.
After more than a decade in the trenches, building everything from fintech platforms to AI-driven health apps, I've learned a thing or two about keeping IP locked down tight. It's a delicate dance, really. You need those external brains, those fresh perspectives that can turn a good product into a great one. But you also need to sleep at night, knowing your secret sauce isn't being served up to the highest bidder.
Understanding the Stakes
Before we dive into specific strategies, it's crucial to understand what's at risk. Your intellectual property isn't just lines of code or design documents; it's the very essence of your competitive advantage. It encompasses your unique algorithms, innovative features, proprietary databases, and even the architectural decisions that make your product stand out.
Consider the case of a fintech startup I worked with recently. They had developed a novel algorithm for real-time fraud detection in cryptocurrency transactions. This algorithm was their golden goose – the key differentiator that set them apart in a crowded market. When they needed to scale rapidly, they decided to bring in external developers to build out their platform. The challenge? How to tap into this external talent without exposing their core IP to potential competitors or bad actors.
The Myth of Complete Control
One of the most common misconceptions I encounter is the belief that you can maintain complete control over your IP when working with external teams. The reality is far more nuanced. The old model of keeping everything behind locked doors is not working in today's interconnected development environment.
Instead of aiming for total control, which can stifle collaboration and slow down development, the goal should be to create a framework that protects your core IP while allowing for efficient and effective collaboration. It's a delicate balance, but one that's achievable with the right approach.
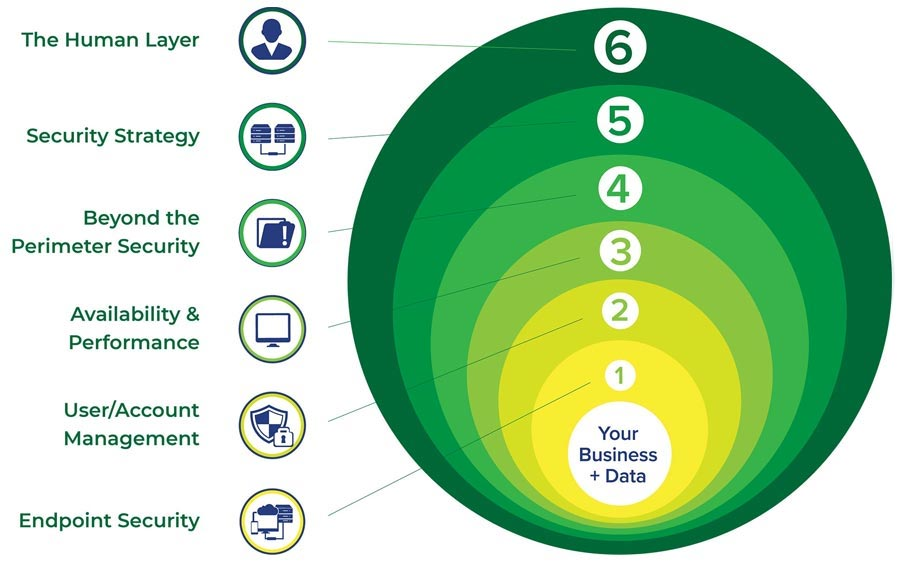
Layered Protection: A Comprehensive Strategy
The most effective approach to IP protection is a layered one. Think of it as a series of concentric circles, with your core IP at the center, surrounded by layers of legal, technical, and operational safeguards. Let's break this down:
| Protection Layer | Key Components | Primary Purpose |
|---|---|---|
| Legal | NDAs, IP Assignment Agreements, Non-Compete Clauses | Establish legal framework for IP ownership and confidentiality |
| Technical | Modular Architecture, Access Control, Code Obfuscation | Implement barriers to unauthorized access and reverse engineering |
| Operational | Selective Outsourcing, Code Reviews, Clear Documentation | Manage day-to-day activities to minimize IP exposure |
1. Legal Foundations
The first layer of protection should always be legal. While contracts alone aren't a silver bullet, they form the bedrock of your IP protection strategy.
Non-Disclosure Agreements (NDAs)
Start with a robust NDA. But here's the catch – a generic NDA won't cut it. I've seen too many companies rely on boilerplate agreements that leave gaping holes in their protection. Your NDA should be tailored to your specific situation, clearly defining what constitutes confidential information, how it can be used, and the consequences of breaches.
For instance, when working with a healthcare startup, we crafted an NDA that specifically addressed the handling of anonymized patient data used in their AI models. This level of specificity not only protects your IP but also demonstrates to your external partners the seriousness with which you approach data security.
Intellectual Property Assignment Agreements
Ensure that all work produced by external developers is explicitly assigned to your company. This agreement should cover not just the final product but also any intermediate work, ideas, or innovations developed during the project.
A cautionary tale: I once worked with a company that neglected to include such an agreement. When one of their external developers left mid-project and started a competing business, they found themselves in a legal gray area regarding ownership of certain features developed during the collaboration.
Non-Compete Clauses
While often controversial and not always enforceable depending on your jurisdiction, carefully crafted non-compete clauses can provide an additional layer of protection. The key is to make them reasonable in scope and duration. For example, prohibiting developers from working on directly competing projects for a specific period after your engagement ends.
2. Technical Safeguards
With legal foundations in place, the next layer involves technical measures to protect your IP.
Modular Architecture
Design your system architecture in a modular fashion. This approach allows you to compartmentalize sensitive components, keeping your core IP separate from the parts that external developers work on.
In practice, this might look like isolating your proprietary algorithm in a microservice with a well-defined API. External developers can then build around this service without needing access to its inner workings.
Access Control and Monitoring
Implement stringent access controls. Use the principle of least privilege – give developers access only to the parts of the system they absolutely need to work on. Coupled with this, implement robust logging and monitoring systems to track who accesses what and when.
A real-world example: For a client in the financial sector, we implemented a system where external developers worked in sandboxed environments. Each environment was tailored to the specific task at hand, with sensitive data obfuscated and core algorithms accessed only through API calls. This approach allowed for efficient development while keeping the crown jewels under lock and key.
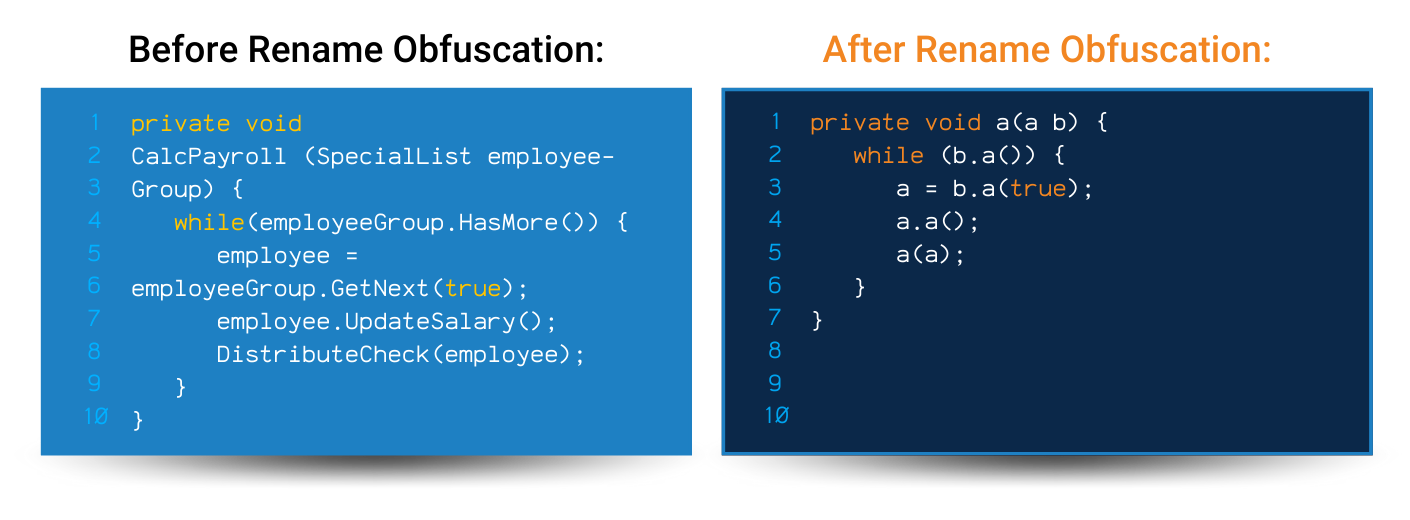
Code Obfuscation and Encryption
For particularly sensitive parts of your codebase, consider techniques like code obfuscation. While not foolproof, it can significantly increase the difficulty of reverse engineering your proprietary algorithms.
Similarly, ensure that all data transfers and storage are encrypted. This is especially crucial when working with remote teams, where data might be transmitted across various networks.
3. Operational Practices
The final layer of protection involves your day-to-day operational practices.
Selective Outsourcing
Be strategic about what you outsource. Keep the development of core IP in-house and use external developers for more generic components or integrations.
For instance, a client in the AI space kept their machine learning model development strictly internal but turned to external talent for building the user interface and data visualization components.
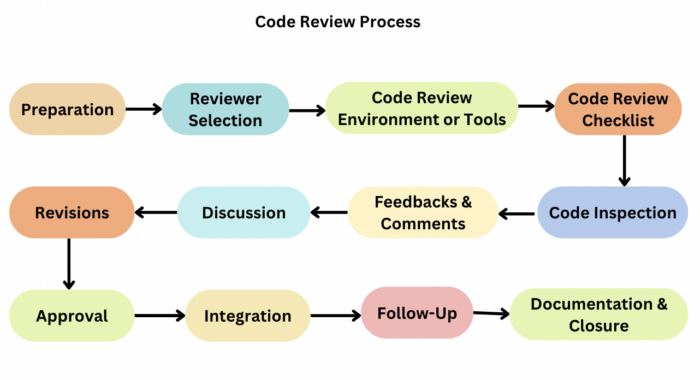
Regular Code Reviews and Audits
Implement a rigorous code review process. This not only ensures code quality but also allows you to monitor what's being developed and how it integrates with your core systems.
Additionally, conduct regular security audits. These can help identify potential vulnerabilities or instances where sensitive information might be inadvertently exposed.
Clear Communication and Documentation
Maintain clear, comprehensive documentation of your systems and processes. This not only aids in development but also clearly delineates what is proprietary and what isn't.
Equally important is clear communication with your external teams. Make sure they understand the sensitivity of the project and the rationale behind your security measures. In my experience, developers who understand why certain restrictions are in place are more likely to respect and adhere to them.
Building Trust While Protecting Assets
One of the most challenging aspects of working with external developers is balancing protection with trust. Overly restrictive measures can lead to inefficiencies and may deter top talent from working with you.
| Trust-Building Measure | IP Protection Impact | Developer Satisfaction Impact |
|---|---|---|
| Transparent Communication | Moderate Positive | High Positive |
| Collaborative Problem-Solving | Low Risk | High Positive |
| Recognition of Contributions | Low Risk | High Positive |
| Clear Expectation Setting | High Positive | Moderate Positive |
| Regular Feedback Sessions | Moderate Positive | High Positive |
The key is to foster a culture of mutual respect and understanding. Be transparent about your concerns and the measures you're taking to protect your IP. At the same time, show trust in your external partners by giving them ownership of their work within the agreed-upon boundaries.
I've found that the most successful collaborations are those where external developers feel like valued partners rather than potential threats. This approach not only protects your IP but also leads to more innovative and effective solutions.
Adapting to Different Development Models
It's important to recognize that different development models require different approaches to IP protection. Let's explore a few common scenarios:
| Development Model | Unique Challenges | Key Protection Strategies |
|---|---|---|
| Offshore Teams | Jurisdictional differences, Cultural norms | Enforceable cross-border agreements, Robust technical safeguards |
| Freelancers | Long-term control, Consistency | Milestone-based contracts, Thorough onboarding, Detailed documentation |
| Development Agencies | Alignment of processes, Tool ownership | Review agency policies, Clarify IP ownership, Knowledge transfer protocols |
Offshore Development Teams
When working with offshore teams, you're often dealing with different legal jurisdictions and cultural norms. In these cases, it's crucial to:
- Ensure your legal agreements are enforceable in the relevant jurisdictions.
- Implement more robust technical safeguards, given the physical distance and potential differences in data protection laws.
- Invest in building strong relationships with team leaders to foster a culture of trust and responsibility.
Freelance Developers
With individual freelancers, the challenges often revolve around long-term control and consistency. Consider:
- Using milestone-based contracts that tie payments to specific deliverables and the transfer of IP rights.
- Implementing a thorough onboarding process that covers your IP protection protocols.
- Maintaining detailed documentation to ensure continuity if the freelancer becomes unavailable.
Development Agencies
When working with agencies, you benefit from their established processes but need to ensure they align with your IP protection needs:
- Review the agency's own IP protection and security policies.
- Clarify ownership of any tools or frameworks the agency might use in your project.
- Establish clear protocols for knowledge transfer at the end of the engagement.
Case Study: Balancing Innovation and Protection
Let me share a recent experience that illustrates these principles in action. We were working with a startup developing a revolutionary supply chain management platform. Their core IP was a set of algorithms that optimized routing and inventory management in real-time.
Here's how we structured the collaboration:
- Legal Framework: We started with a comprehensive NDA and IP assignment agreement. The agreements were specifically tailored to cover algorithm designs, data models, and any innovations arising from the project.
- Architectural Approach: We designed the system with a clear separation between the core algorithmic engine and the surrounding application. The external team focused on building the user interface, data visualization tools, and integration layers.
- Access Control: We implemented a tiered access system. The external team worked primarily with anonymized data and accessed the core algorithms through a carefully designed API.
- Code Management: We used a private GitHub repository with granular access controls. Regular code reviews ensured that no sensitive information was inadvertently pushed to the repository.
- Knowledge Sharing: Instead of sharing the algorithms themselves, we provided detailed specifications of inputs, outputs, and performance characteristics. This allowed the external team to integrate effectively without exposing the proprietary details.
- Continuous Monitoring: We implemented automated scanning of code commits for potential IP leaks and regular security audits.
The result? A successful collaboration that delivered a cutting-edge product while keeping the client's core IP secure. The external team felt valued and integrated, while the client maintained control over their key differentiators.
| Vulnerability | Risk Level | Mitigation Strategy | Implementation Complexity |
|---|---|---|---|
| Source Code Theft | High | Code obfuscation, Segmented access | Medium |
| Data Breaches | High | Encryption, Access logging | Medium to High |
| Insider Threats | Medium | Background checks, Least privilege access | Low to Medium |
| Reverse Engineering | Medium | API-only access to core functions, Legal deterrents | High |
| Accidental IP Disclosure | Low | Clear documentation, Regular training | Low |
The Future of IP Protection in Collaborative Development
As we look to the future, several trends are shaping how we approach IP protection in collaborative development:
AI and Machine Learning
As AI becomes more prevalent in development, new challenges arise. How do you protect IP when your core asset is a trained model? This requires new approaches to data handling, model deployment, and even the legal definition of intellectual property.
Blockchain and Smart Contracts
Blockchain technology offers interesting possibilities for IP protection. Smart contracts could potentially automate aspects of IP assignment and licensing, providing a transparent and immutable record of ownership and usage rights.
Zero-Trust Security Models
Moving beyond traditional perimeter-based security, zero-trust models assume no implicit trust, even within the organization. This approach, while complex to implement, offers robust protection for distributed development teams.
A Balanced Approach
Protecting your intellectual property when working with external developers is not about building impenetrable walls. It's about creating a framework that safeguards your core assets while enabling productive collaboration.
The most successful approaches combine:
- Robust legal protections
- Smart technical measures
- Thoughtful operational practices
- A culture of trust and mutual respect
Remember, your goal is not just to protect your current IP but to create an environment where innovation can thrive. By implementing these strategies, you can confidently recruit external talent to accelerate your development while keeping your crown jewels secure.
Regularly review and update your IP protection strategies to ensure they keep pace with technological advancements and changing business needs. With the right approach, external collaboration can be a powerful tool for innovation, driving your business forward while keeping your intellectual property safe and sound.



