How Can We Ensure Data Security When Working With External Developers?
Make data security a no-compromise deal when working with outsourced developers. Here's how!

Data security is not just an IT issue. It’s a business imperative. When you entrust external developers with your code, your systems, or even a glimpse of your operations, you’re taking a calculated risk. It’s a bit like giving someone the keys to your house. Trust is essential, but safeguards? Non-negotiable.

At 1985, an outsourced software development company, I’ve seen the best and worst of data security practices. We’ve helped clients rescue projects sabotaged by breaches, and we’ve built robust systems for businesses that understood security as a competitive edge. In this post, I’ll share what works, what doesn’t, and how you can sleep better at night knowing your data is safe.
Start With Contracts That Mean Business
Let’s face it. Contracts can feel like legal fluff. But when it comes to data security, they’re your first line of defense.
Why Contracts Matter More Than You Think
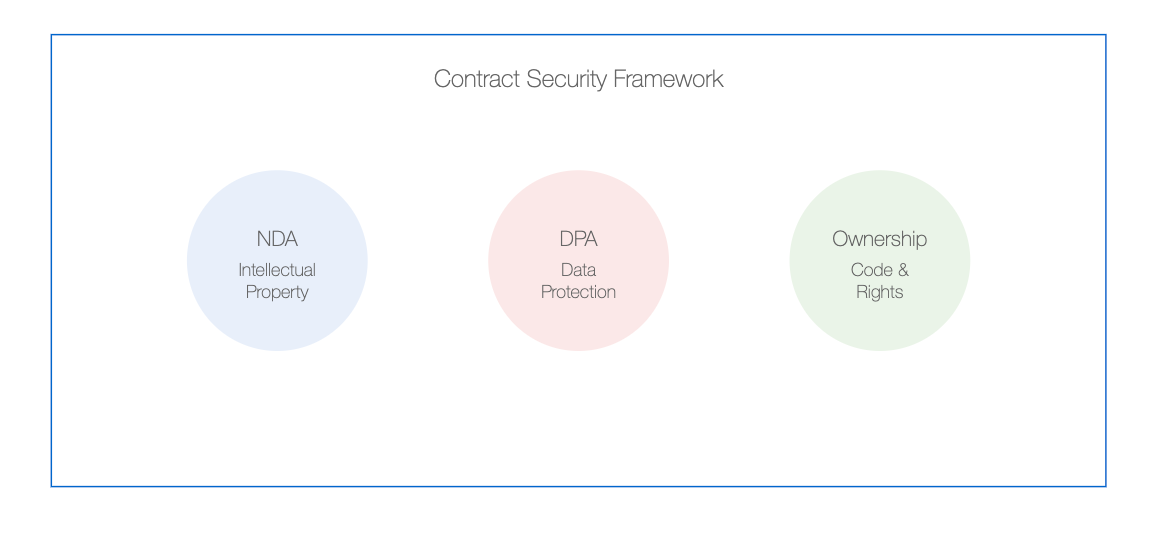
A good contract isn’t just a handshake in writing. It’s a fortress. It sets expectations, defines boundaries, and clarifies consequences. For example:
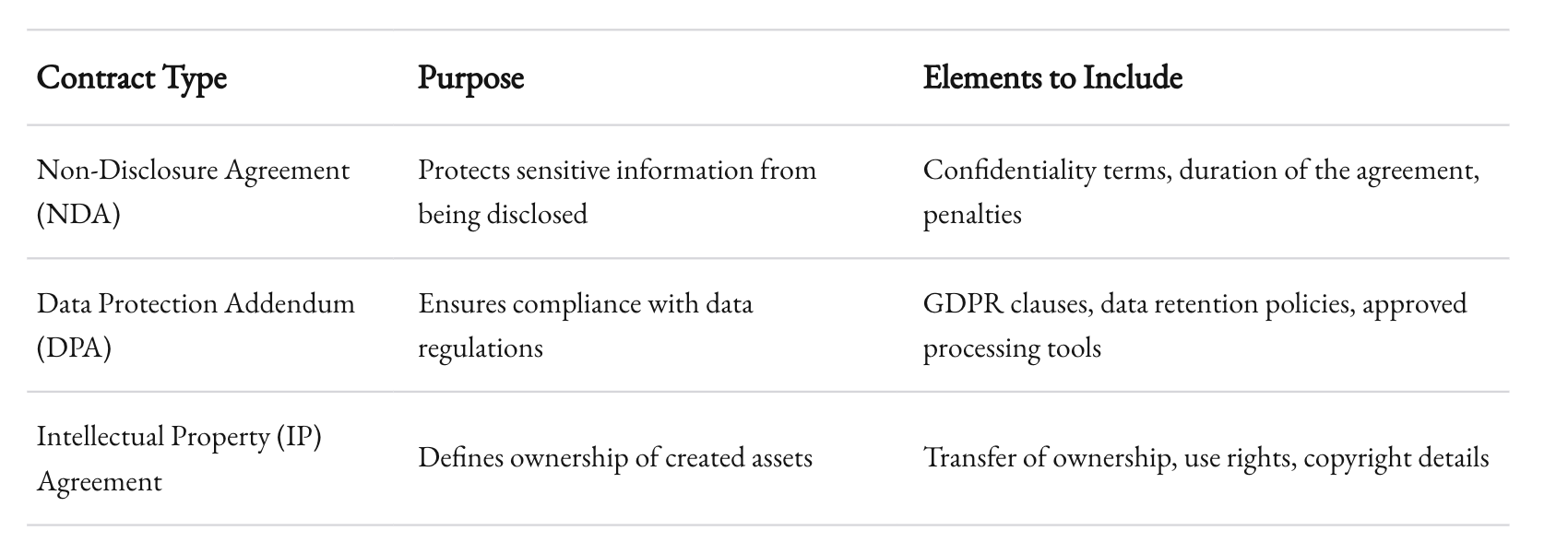
- NDAs (Non-Disclosure Agreements): These ensure your intellectual property doesn’t wander into the wild.
- Data Protection Addendums (DPAs): Required for GDPR or similar regulations, these bind developers to your data-handling rules.
- Clear Ownership Terms: Spell out who owns the code and intellectual property (hint: it should be you).
Without these, you’re exposed. Worse, you’re inviting disputes over who’s responsible if something goes wrong.
Actionable Insight
Ask your legal counsel to tailor contracts specifically for working with external developers. Cookie-cutter templates won’t cut it. Mention specifics: permissible tools, storage locations, and incident response times. If you’re unsure, there’s no shame in over-specifying.

Vet Developers Like You’re Hiring for the CIA
Every developer isn’t created equal. Skills matter, but so does integrity. When external developers touch your data, due diligence isn’t optional.
Beyond Technical Interviews
Most companies stop at evaluating technical skills. That’s a mistake. A technically gifted developer with a poor sense of security can be a liability.
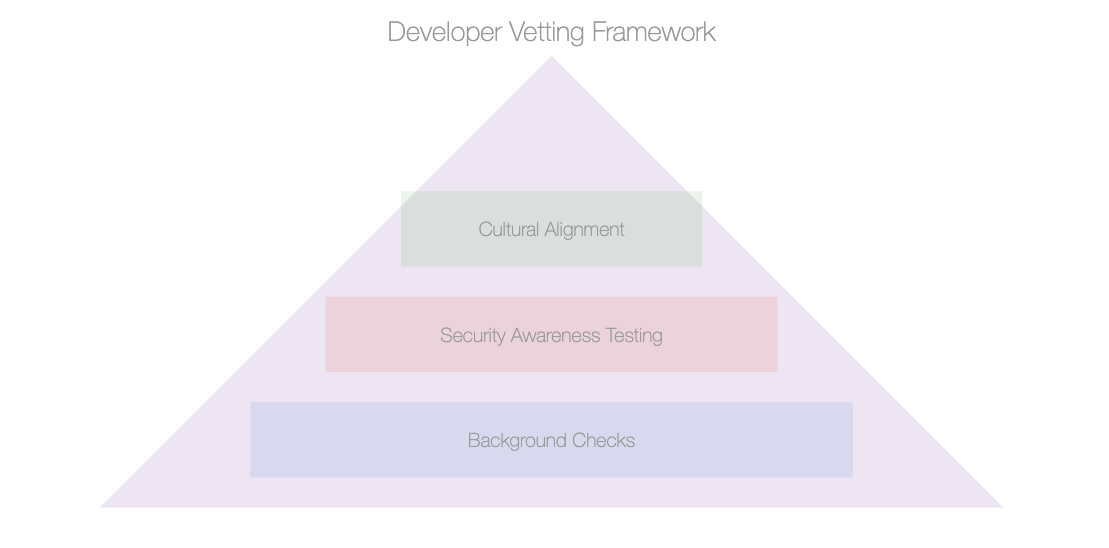
Here’s what your vetting process should include:
- Background Checks: Verify their work history and client references.
- Security Awareness Testing: Do they know secure coding principles? Ask them.
- Cultural Alignment: Developers should align with your company’s values, including how seriously you take security.
The Red Flags to Watch For
- Ambiguity About Past Work: Developers who dodge questions about past projects might be hiding something.
- Too-Good-To-Be-True Pricing: Cheap rates often mean shortcuts. And shortcuts in security can cost you millions.
- Reluctance to Use Secure Channels: Developers who insist on using unsecure communication or collaboration tools are risks waiting to happen.
Actionable Insight
Run mock scenarios during onboarding. For example, simulate a data breach and gauge their response. It’s not about passing or failing; it’s about knowing how they think under pressure.
Segregate, Don’t Concentrate
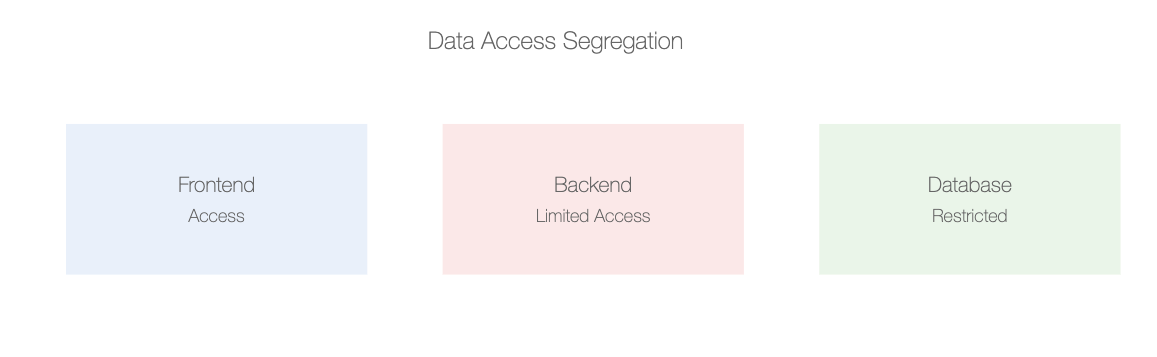
When developers work with your data, do they really need access to everything? Probably not.
Principle of Least Privilege (POLP)
This is your guiding light. POLP means giving access only to the data and systems necessary to perform their job. Nothing more. Nothing less.
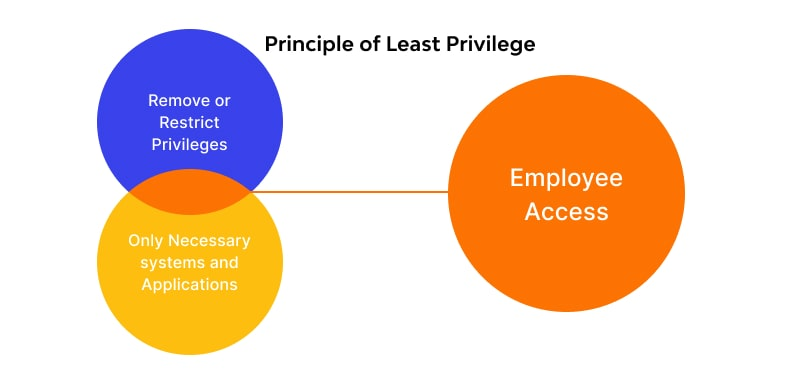
For instance:
- Don’t give a frontend developer access to the backend database unless absolutely necessary.
- Use environment-specific data. Staging or test environments should contain dummy data, not production secrets.
Tech to the Rescue
Modern tools can enforce these principles:
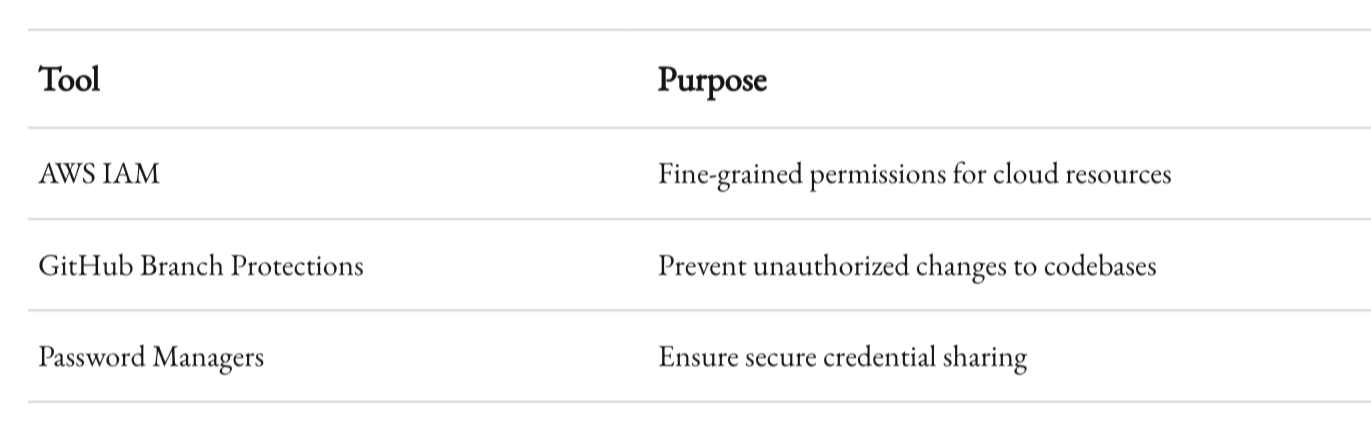
Actionable Insight
Conduct periodic access audits. People’s roles evolve, but permissions often don’t. Revoke access when no longer needed.
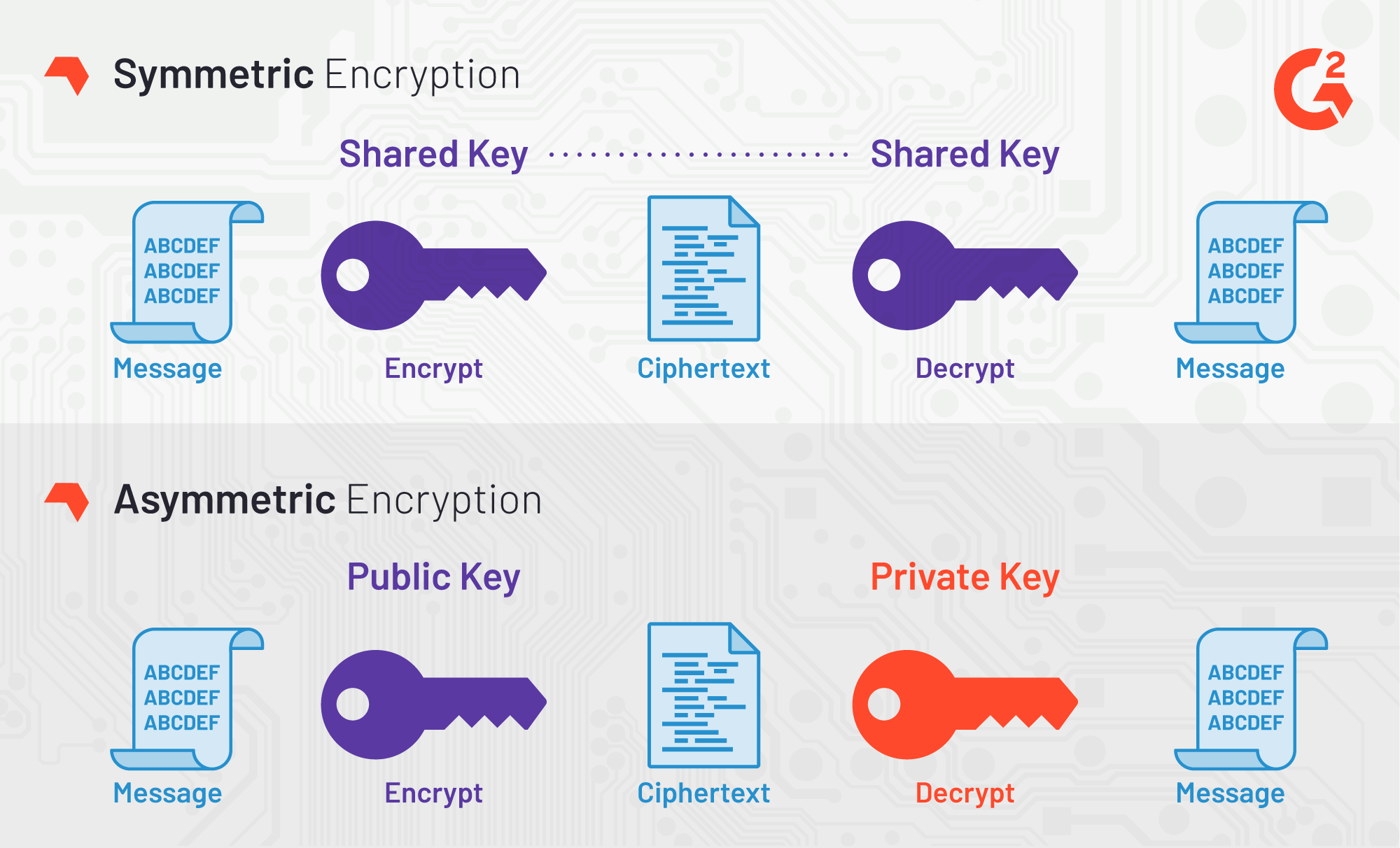
Encrypt Everything, Assume Nothing
Encryption might seem like overkill. It’s not. In fact, it’s the bare minimum.
End-to-End Encryption (E2EE)
When you share sensitive data with external developers, ensure it’s encrypted from the moment it leaves your system to the moment they receive it. Tools like Signal or encrypted email services like ProtonMail can handle this seamlessly.
Encrypt in Transit and At Rest
Data is most vulnerable when it’s moving or idle. Make sure you:
- Use HTTPS for all web communications.
- Encrypt databases with industry standards like AES-256.
Actionable Insight
Set up automated scans to check for unencrypted connections or files. There are tools like Qualys or Nessus that can identify weak spots in your encryption setup.

Monitor and Log Everything
Trust is good. Logs are better. Knowing who accessed what and when can make all the difference if something goes wrong.
What to Log
Log everything. Specifically:
- Codebase Access: Track who cloned, pulled, or pushed to repositories.
- Server Logins: Record every access attempt, successful or failed.
- File Transfers: Keep tabs on who downloaded sensitive files.
Use Centralized Tools
Here are some tools that can simplify monitoring:
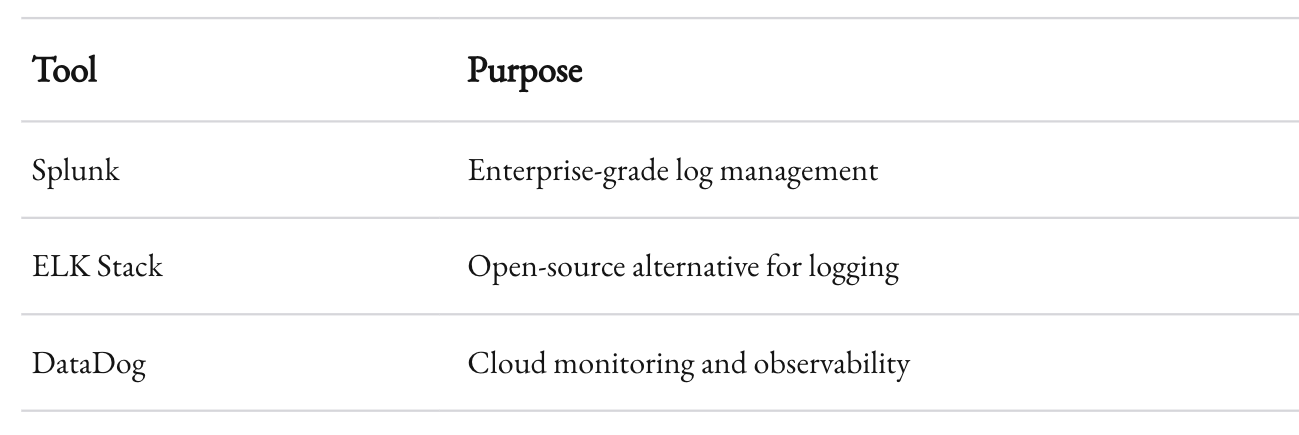
Actionable Insight
Set up alerts for unusual activity. For example, if a developer accesses sensitive data at 2 AM, you should know about it.
Educate and Evolve
Security isn’t static. Threats evolve, and so should your practices. The best investment you can make is in education.
Continuous Security Training
Even experienced developers benefit from ongoing training. Cover topics like:
- Recognizing phishing attempts.
- Secure coding standards.
- Incident response protocols.
Create a Feedback Loop
Encourage developers to report potential security flaws. Reward them for finding vulnerabilities before malicious actors do.
Actionable Insight
Host quarterly “security drills.” Make them collaborative. Not punitive. Use these drills to refine processes and identify weak points.
Security as a Partnership
Working with external developers doesn’t have to feel like walking a tightrope. With the right safeguards, it can be a partnership rooted in trust and resilience. Start with solid contracts. Vet developers like your business depends on it (because it does). Limit access, encrypt data, and monitor everything. And above all, stay adaptable. Security is a journey, not a destination.
At 1985, we’ve built our reputation on safeguarding the interests of our clients. If there’s one thing we’ve learned, it’s this: Security isn’t a cost. It’s an investment in trust.



